Important Announcements and Notes
Outdated technical features are subject to removal in order to keep the CloudGen Firewall up to date and performing properly. See the following two paragraphs for the features that will be removed in this release and the features that are subject to removal in upcoming releases.
Certain features will be removed completely because they have become technically obsolete; other features have become outdated and will be replaced by improved technology.
CloudGen Access Proxy
Features That Will Become Obsolete in an Upcoming Release
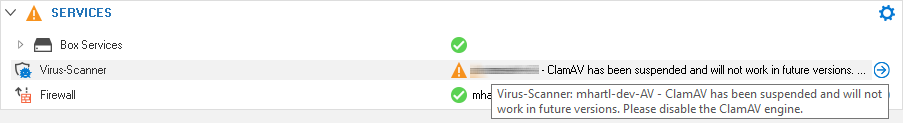
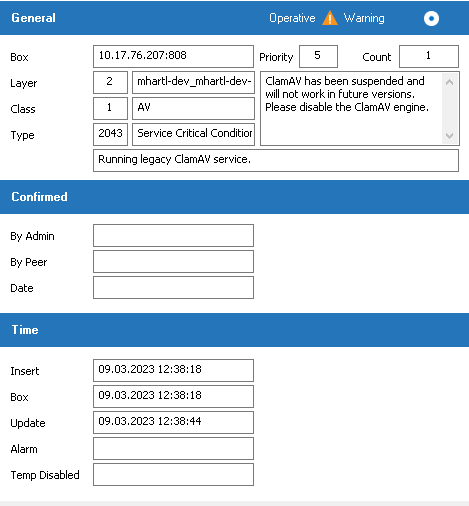
Virus Scanning with ClamAV
Note that until the final removal of ClamAV, the firewall will start the service; however, the service will be highlighted with a warning notifying the customer about the deprecation.
Also, an appropriate event will be created:
Use the Appropriate Firewall Admin Release
Barracuda Networks recommends using the latest version of Firewall Admin for a new firmware release.
As of the public availability of firmware 9.0.1, Barracuda Networks recommends using at least Firewall Admin version 9.0.1. You can download this version here: https://dlportal.barracudanetworks.com/#/packages/5700/FirewallAdmin_9.0.1-120.exe.
IMPORTANT BEFORE UPDATING
Different Python Versions on Former Firmware Releases
Python scripts accompany every firmware release and control the migration process from one firmware to a newer version. Because the Python system is also distributed in different versions at certain times, the CloudGen Python scripts as part of a new CloudGen firmware also vary over time.
If you are operating firmware 8.0.x and want to migrate your firewall to firmware 9.0.1, you must first update from firmware 8.0.x to 8.3.2. Then, you can continue to upgrade from firmware 8.3.2 to 9.0.1.
If you are operating firmware 8.2.x - 9.0, you can directly migrate to firmware 9.0.1.
For details and more information, see the 9.0.1 Migration Notes.
Release Notes
Firmware version 9.0.1 is a minor release.
EoL and EoS Status
For information on which devices and services have reached EoL or EoS status, see:
- Barracuda NextGen and CloudGen Firewall Appliances - EoS / EoL Definitions
- End-of-Support for CloudGen Firewall Firmware
What's New in Version 9.0.1
Resizable View for Box Licenses
The view for listing the box licenses no longer is static and now provides the option to resize the columns and thus the size of the overall view.
For more information, see 9.0.1 Release Notes for Barracuda Firewall Admin, Release 9.0.1-120, November 2023.
Simplified Traffic Shaping
The number of default shaping connectors available for out-of-the-box traffic management has been reduced to four: High, Medium, and Low with a bandwidth ratio of 4:2:1, and Realtime.
For more information, see Traffic Shaping.
Configurable Memory Monitoring
The configuration area for performance like CPU load, hardware, and disk has been extended and now contains a section for configuring memory monitoring.
For more information, see How to Configure CPU Load, Hardware, Disk, and Memory Monitoring.
Linking a Repository to a Default Box Node
As of firmware 9.0.1, it is possible to link a repository node to its name-related Default Box node. This option increases the speed of configuring a larger number of firewalls based on commonly used settings. Settings that are less used can still be configured individually with little effort.
For more information, see Example - How to Link a Cluster/Global Repository Node to a Default Box Node.
New Binary File Format for PAR Files
The list of former PAR file types has been extended and now contains a new, binary-encoded file type with the suffix .ppe
For more information, see How to Back Up and Restore Firewall, Secure Access Controller, and Control Center Configurations.
General Term Replacement of SSL Inspection to TLS Inspection
The term SSL has been replaced by the more appropriate term TLS at all relevant places in the user interface. All related articles have been updated accordingly.
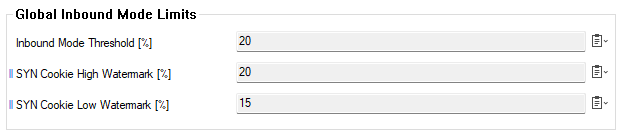
Dedicated Configuration Section for Global Inbound Mode Limits
Because the global inbound mode settings do not need a firmware or service restart to take effect, the configuration section can now be accessed via the path CONFIGURATION > Configuration Tree > Infrastructure Services > General Firewall Settings.
| Former Section for Settings | New Section for Settings |
|---|---|
 |
This section no longer requires a restart of the host firewall service to take effect. |
For more information, see General Firewall Configuration, paragraph Global Inbound Mode Limits.
Naming of Network Objects
The former naming of Network Pool Object has been changed and is now called Pool Object.
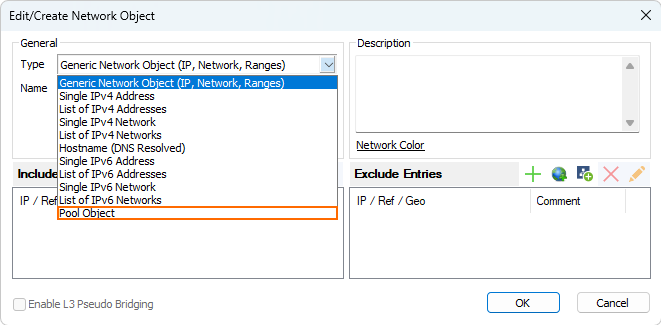
For more information, see Network Objects and How to Create a Pool Object.
Additional SSD for Logging
The F1000b model allows inserting an additional SSD/HDD into the extension slot on the front of the housing.
Licensing, Pool Licenses
Previously, pool licenses could be managed only on a global level in a Control Center. As of firmware release 9.0.1, pool licenses can be configured so that administrators are allowed to handle them on a range or cluster level. To allow administrators with a specific scope to view and assign pool licenses within their range/cluster, global administrators must define the range/cluster for each pool license.
For more information, see How to Allow Administrators with a Limited Scope to Use Pool Licenses.
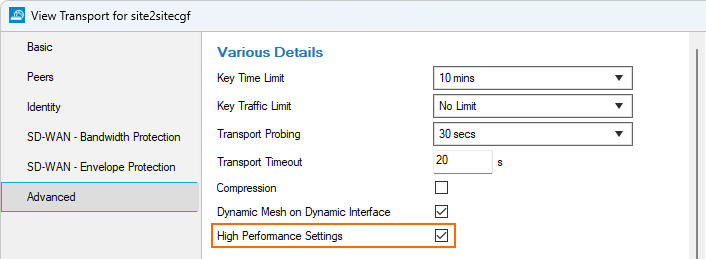
VPN Site-to-Site High-Performance Settings Enabled by Default
CloudGen Firewalls operating with multiple CPUs generally provide higher performance. When using VPN TINA tunnels, the higher hardware performance of multiple CPUs can provide a better transmission rate on TINA tunnel transports.
The option High Performance Settings is therefore enabled by default for CloudGen Firewalls operating with multiple CPUs for VPN TINA tunnel transports.
Updates to Policy Profiles
In URL Filtering Policies, the actions Alert and Warn and Continue are now available. Their functionality is the same as in URL Filter Policy Objects for CGFs with Application Rules enabled.
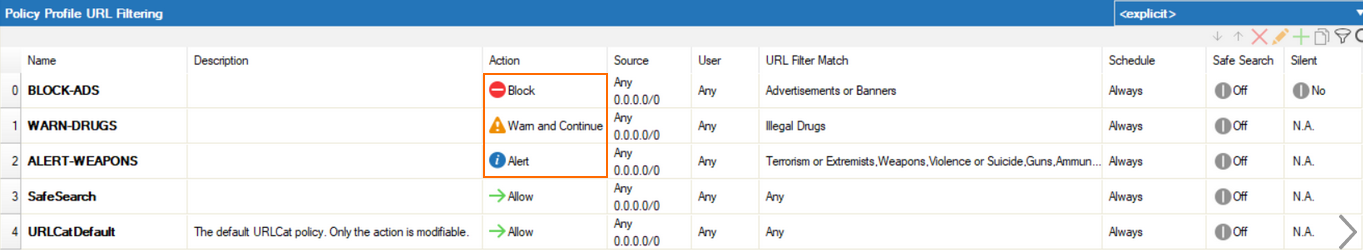
SafeSearch Enforcement is now available for CGFs in Policy Profiles mode and can be selected in the URL Filtering Policies.
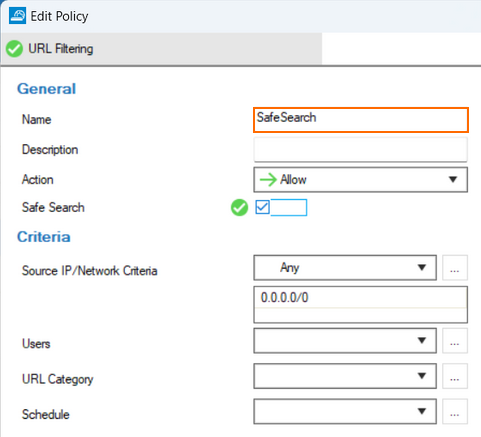
For this setting to take effect, the corresponding URL Filtering rule must match traffic to search engines. In addition, TLS Inspection must be enabled.
Supported search engines:
- Yahoo
- Bing
- YouTube
- DuckDuckGo (new in 9.0.1, also for CGF with app rules)
The new setting for Silent Blocking only affects the Secure Edge Agent. If it is enabled, no pop-up messages are shown when the gateway blocks a request from the agent based on this rule.
This setting is only available if the action for the rule is set to Block.
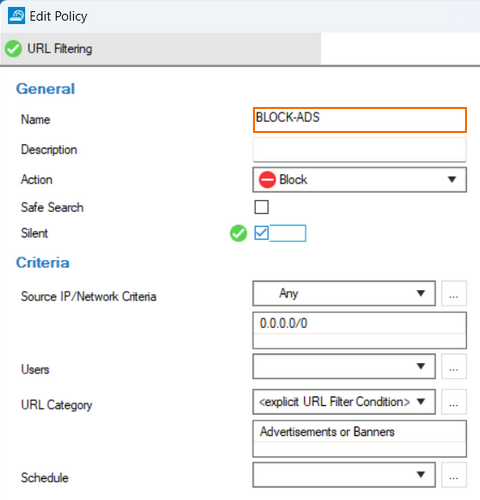
For more information on URL filtering policies, see URL Filtering Policies.
Additions to Security Settings
The Webmonitor feature allows the monitoring and logging of search engine queries for certain keywords. If a user searches for a term marked as monitored:
- a firewall event is generated
- a logline in Assigned Services / <Firewall Service> / web monitor is created
Four categories of monitoring keywords are already predefined. The administrator can configure additional keywords. For this feature to work, TLS Inspection must be enabled. The supported search engines are the same as for SafeSearch.
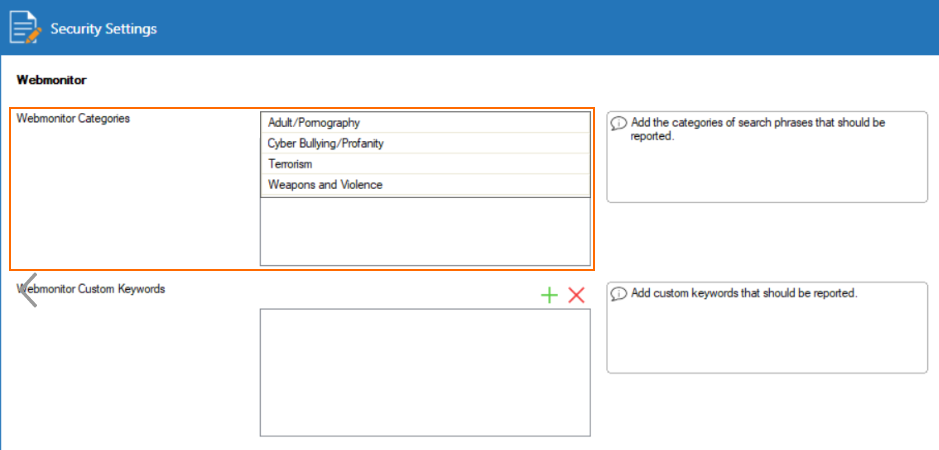
For more information, see How to Configure Web Monitoring Policies.
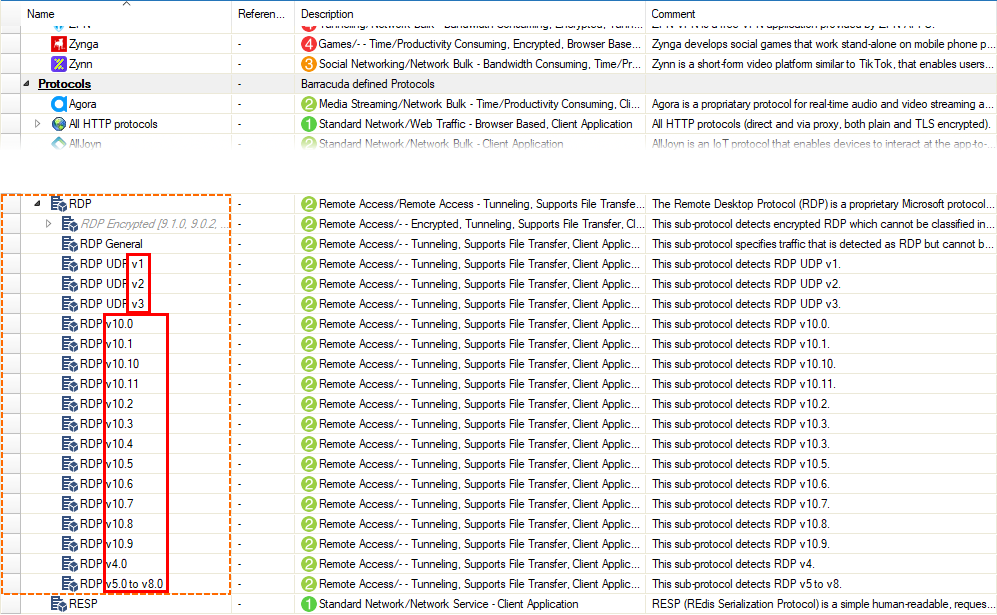
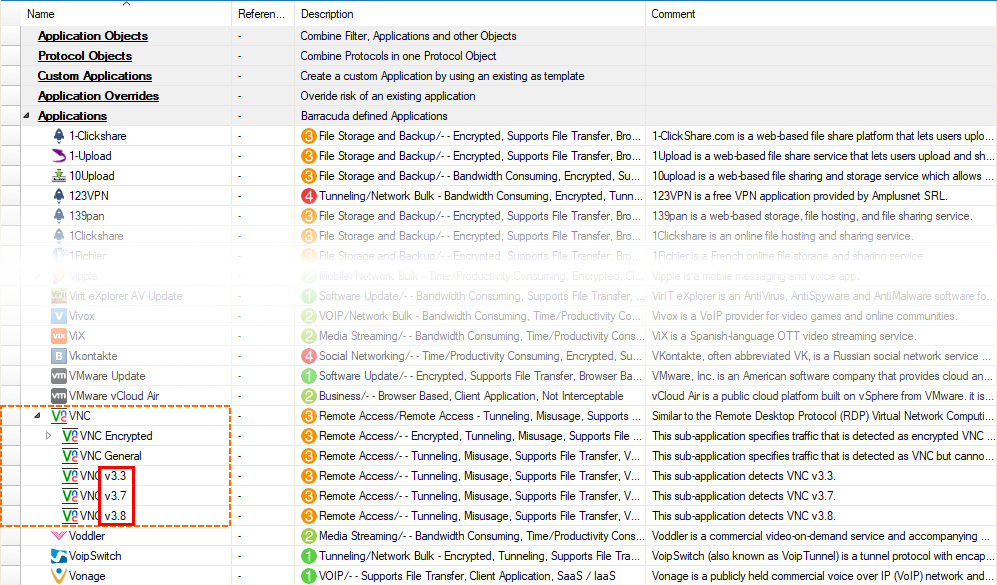
Version Information for Protocols RDP and VNC
The display of the protocols RDP and VNC now includes information on the protocol version.
| RDP | VNC |
|---|---|
|
|
SMTPS for System Notification
Sending system notifications now supports SMTPS.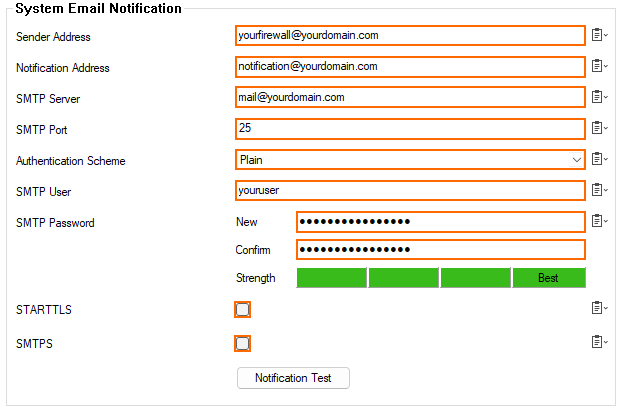
For more information, see How to Configure System Email Notifications.
Improvements Included in Version 9.0.1
Authentication
- The DC-client process no longer causes high CPU loads if data transfer gets interrupted. [BNNGF-79083]
- Usernames in TOTP are no longer case-sensitive. [BNNGF-82953]
- DC Agent timeouts now work as expected on subsequent logins. [BNNGF-84267]
- In the authentication system, groups are now handled correctly for usernames containing special characters. [BNNGF-87929]
- The validation of certificates no longer causes issues in certain situations. [BNNGF-88317]
- SAML authentication now works as expected. [BNNGF-89482]
- Using Explicit Groups in authentication now works as expected. [BNNGF-90056]
Redirecting authentication now works as expected. [BNNGF-90102]
When enabling signing and encryption for SAML, the presence of certificates is checked, and Firewall Admin raises an error message if the configuration with missing certificates is attempted to be activated. [BNNGF-91454]
Barracuda Firewall Admin
- Creating and restoring backups with PAR files now supports the new binary file type
.ppe. [BNNGF-78047] - Firewall Admin no longer crashes randomly in certain situations. [BNNGF-84184]
- Licenses are now correctly displayed for HA pairs in the Control Center. [BNNGF-84394]
- The Access Control Service no longer crashes in certain situations. [BNNGF-87583]
- The visibility of referenced policies in the managed box firewall tab has been optimized. [BNNGF-88425]
- Barracuda Firewall Admin no longer crashes in certain situations. [BNNGF-88485]
- Copying an IP address from a firewall rule using the Copy <IP> to Clipboard feature and applying it as a filter in the Firewall View (live or history) now works as expected. [BNNGF-88674]
- Barracuda Firewall Admin no longer crashes under high latency and high system load. [BNNGF-88735]
Incorrect error messages are no longer displayed for any new URL CAT policy. [BNNGF-89391]
Migrating a ruleset from an app to a policy-based ruleset now works as expected. [BNNGF-89393]
It is no longer possible to revert from a policy-based ruleset to an application ruleset in the firewall feature settings. [BNNGF-89402]
Firewall Admin no longer displays incorrect UI items after making changes to an SD-WAN policy. [BNNGF-89449]
Dynmesh can now be set per transport as expected. [BNNGF-89468]
SD-WAN ID issues no longer occur in GTI. [BNNGF-89473]
GTI now shows bi-directional connection arrows for active-active transports. [BNNGF-89479]
Barracuda Firewall Admin no longer crashes if a user closes a tab. [BNNGF-89499]
Barracuda Firewall Admin no longer crashes while making changes to access rules. [BNNGF-89545]
Barracuda Firewall Admin now entirely displays the SSL settings for the current connection. [BNNGF-89903]
- SSL Inspection has been renamed to TLS Inspection. [BNNGF-89907]
- If no updates are available, the item for Automated Security Updates now displays
No recent updatesas expected in the status element of the DASHBOARD. [BNNGF-89989] - Watermarks for memory monitoring are no longer static and are now configurable in Firewall Admin. [BNNGF-90076]
- Barracuda Firewall Admin no longer erroneously displays messages that no group patterns are configured if they have been configured correctly. [BNNGF-90117]
- The editor window for named networks shows network addresses in CIDR notation as expected. [BNNGF-90305]
- GTI is now displayed for firmware versions lower than 9.0.0 when using the newest Firewall Admin version. [BNNGF-89002], [BNNGF-90316]
If a provider has been configured for a transport, Firewall Admin will not display/write the bind interface. [BNNGF-90340]
When creating an application object, applications are now listed as expected. [BNNGF-90349]
- The descriptions for WCS 3.0 categories are now displayed as expected. [BNNGF-90451]
The edit field for entering new group names for the pre-authentication scheme now accepts the '.' character for the mapping scheme. [BNNGF-90756]
User agents are now loaded as expected. [BNNGF-90783]
Various stability fixes have been done so that Firewall Admin no longer crashes in certain situations. [BNNGF-90826] [BNNGF-90828]
Firewall Admin no longer crashes if an administrator tries to access the Firewall Monitor tab. [BNNGF-90979]
The filter drop-down menu for hotfixes now works as expected. [BNNGF-91048]
- The configuration settings for inbound mode limits can now be accessed at CONFIGURATION > Configuration Tree > Infrastructure Services > General Firewall Settings. [BNNGF-91136]
The naming of 'Pool Network Objects' has been updated to 'Pool Object'. [BNNGF-91140]
The display view for application objects now displays all applications as expected. [BNNGF-91980]
The '@' character can now be used for usernames in VPN configurations. [BNNGF-92050]
Barracuda OS
- DHCP Relay now uses the correct type of IP address and works as expected. [BNNGF-71929]
- Wi-Fi configuration files are now processed correctly. [BNNG-76329]
- In an HA pair, the firewalls no longer show a 'dirty sync' message for the pattern updates after migrating to the two-layer architecture. [BNNGF-81626]
- Login events no longer cause firewall rules to fail in certain situations. [BNNGF-82853]
- Logging options for the CGA Proxy have been improved. [BNNGF-85954]
- The firewall no longer freezes in the boot phase if more than 1000 routes are configured. [BNNGF-86079]
- Sending system notifications now supports SMTPS (port 465). [BNNGF-86272]
- The Network activation required dialog no longer shows up after a site-specific network is edited. [BNNGF-87084]
- The Barracuda Reporting Server daemon now increases the time between retries if the connection cannot be established. [BNNGF-87177]
- Firewalls no longer send data if Firewall Insights does not respond. [BNNGF-87850]
- Source-based thrown boot routes are no longer removed with a soft activation. [BNNGF-87926]
- IPMI logs no longer show errors after updating the IPMI firmware. [BNNGF-88127]
- The
snmpwalknow matches with the tunnel state as expected. [BNNGF-88542] - The
qedeethernet driver is installed and now works as expected. [BNNGF-88581] - After creating an SC box with ConfTemplates, the SC firmware update over CC now works as expected. [BNNGF-88646]
- The tunnel interfaces are now set up in the Shared Networks and IPs section as expected. [BNNGF-89085]
- MAC addresses are exchanged correctly during an HA failover if a real interface is part of a bond interface. [BNNGF-89137]
- Spaces and the underscore character are now allowed in usernames. [BNNGF-89238]
Bond interfaces no longer need to work in promiscuous mode and now work as expected after being configured as an ordinary bond interface. [BNNGF-89266]
- As Mexico no longer has daylight-saving time, the correct time is set for America/Mexico City. [BNNGF-89326]
- The configuration of custom IPFIX templates now works as expected. [BNNGF-89327]
After an update to firmware 9.0.0, the configured networks are propagated with the BGP setup as expected. [BNNGF-89411]
The integrity check now works as expected with firmware 9.0.0. [BNNGF-89833]
- The performance of using pool licenses has been improved. [BNNGF-89410]
Bond interfaces now work as expected for hardware firewalls. [BNNGF-89895]
- The Access Control Service is available for CC-managed F80 firewalls. [BNNGF-89976]
- Syslog streaming to the Control Center works as expected. [BNNGF-90662]
- phionctl services start as expected. [BNNGF-90078]
The firewall no longer generates erroneous alert events about the fan and the power supply. [BNNGF-90114]
WAN connections are no longer disconnected in certain situations. [BNNGF-90177]
The statistics collector now works as expected. [BNNGF-90296]
When updating HA systems with CloudGen Access Proxy enabled, you must reconfigure the proxy to generate a new enrollment URL. [BNNGF-90315] [BNNGF-92169]
SNMPv3 is no longer blocked by the default ruleset. [BNNGF-90338]
- When in stateless mode, the prefix delegation is now applied on the interface that has been set up when it is being received via router advertisements. [BNNGF-90474]
The ping command is now supported for IPv6. [BNNGF-90779]
The log entries for IPv6 management tunnel probing have been improved. [BNNGF-90780]
- SQL requests now work as expected. [BNNGF-90952]
- The assignment of a correct IP address to the LTE modem works as expected. [BNNGF-91157]
The section view for administrative roles no longer shows the deprecated Mail Gateway service. [BNNGF-91198]
Cloud
- The OMS update as part of the install update now works as expected. [BNNGF-89304]
Cloud Google
- When deploying a new CGF in the Google Cloud,
sshpublic keys are set considering both the Google standard for project-widesshkeys and individual custom keys. [BNNGF-88599]
Control Center
- CC Admin now configures firewall rules as expected. [BNNGF-83248]
- Changing the CC Admin password now works as expected. [BNNGF-85237]
- Firmware migration no longer causes issues in certain situations. [BNNGF-85832]
- Dummy changes for the Box Properties node and the IPS configuration node no longer occur in certain situations. [BNNGF-86917]
- Boxes now show up correctly on the Status Map. [BNNGF-87058]
- In the licensing tab on the Control Center, licenses are now displayed to be valid if the base license is valid. [BNNGF-87083]
- Broken VPN/GTI references no longer occur in HA clusters with dedicated HA box configurations. [BNNGF-88141]
- The Status Map no longer shows firewalls after their removal in the configuration tree. [BNNGF-88275]
- When an HA box is deleted, it is now properly removed from the internal database. [BNNGF-88755]
- The RCS Revert option for configuration templates in Firewall Admin now works as expected. [BNNGF-89105]
- The CC Status tab in Barracuda Firewall Admin no longer crashes in certain situations. [BNNGF-89278]
- Default nodes can now be linked to a repository as expected. [BNNGF-89387]
- FQDNs are now allowed to be entered for the syslog destination. [BNNGF-89405]
- Destination/Redirection with site-specific Global Objects now works as expected. [BNNGF-90615]
DHCP
- The HTTP Proxy now handles large POST requests as expected. [BNNGF-87087]
- The DHCP advanced configuration now delivers correct values. [BNNGF-87089]
- Default routes are correctly introduced for DHCPv6 addresses. [BNNGF-89850]
- The DHCP relay starts as expected. [BNNGF-90029]
- When adding or removing an existing interface to the DHCP relay configuration, the service is restarted as expected. [BNNGF-90885]
DNS
- The DNS service now loads external and internal listeners and zones as expected. [BNNGF-83381]
Firewall
Traffic for Windows updates on port 80 now hits the correct app detection rule in the firewall. [BNNGF-82223]
Entries in the firewall activity log file are now processed and now differentiate correctly between Local Block/Local Deny, and forwarding Block/Deny. [BNNGF-85414]
- The display of the protocols RDP and VNC now includes information on the protocol version. [BNNGF-85434]
- Link protection has been improved for HTML emails with links that contain line breaks. [BNNGF-85474]
- Traffic to an SQL server is now forwarded as expected. [BNNGF-86077]
- Replacing a single certificate after a whole certificate chain file was imported now works as expected. [BNNGF-86558]
- Traffic redirected to destination 0.0.0.0/0 will never be sink-holed. [BNNGF-88289]
- The host firewall access rule for allowing traffic on the DHCP interface now also includes xDSL interfaces in the inbound rule. [BNNGF-88467]
- The Schedule firewall object works as expected. [BNNGF-88562]
- Comments are now in the right place after importing a Network Object from a CSV file. [BNNGF-88777]
- A rare race condition has been fixed for the application detection. [BNNGF-89150]
- When the VPN service is active, all routes are now shown correctly on CONTROL>Network. [BNNGF-89308]
- The traffic for the Teams application is now recognized correctly. [BNNGF-89834]
- The type of service is copied correctly in the case of IFWD, PRX, and IPRX. [BNNGF-90044]
Sessions from dynamic rules are now correctly terminated when the dynamic rule expires or is disabled. [BNNGF-91184]
The synflood-protection value Server-Default now works as expected. [BNNGF-91455]
- Binding the resolver connection to the DNS caching service no longer blocks other services. [BNNGF-91666]
HTTP Proxy
- The proxy server no longer supports SHA1 certificates and now requires SHA256 certificates. [BNNGF-89207]
- Emails with attachments from mobile devices are handled as expected if AV is enabled in the reverse proxy. [BNNGF-91199]
NGInstall
- If NGInstall fails to format a USB drive, it will retry several times, and if this also fails, a dialog will give detailed information about the cause. [BNNGF-89602]
Policy Profiles
- Trusted LAN rules now match as expected when used in the IPS, malware, and TLS policies. [BNNGF-89593]
Report Creator
- IPS Report now shows intrusions in readable text instead of IDs. [BNNGF-87086]
REST
- The REST API queries now work as expected for LDAP and MSAD. [BNNGF-87508]
- A configuration change on a firewall ruleset via REST now correctly adapts the ruleset ID. [BNNGF-88263]
- If a box is created using REST with Firewall Admin, validation messages will be shown as warnings instead of errors when applicable in certain situations. [BNNGF-90314]
- A REST endpoint for Remote Execution has been created. [BNNGF-91367]
Virus Scanner
- Scanned ATP files are removed as expected. [BNNGF-85957]
- A notification window is displayed that informs the user that ClamAV is deprecated, and an event will be created. [BNNGF-88471]
- ATP Scan now works as expected with archives that contain large numbers of PDF files. [BNNGF-91336]
VPN
- The start time of a site-to-site VPN tunnel is now set correctly. [BNNGF-57556]
- The QoS band is now shown in the Live view as expected. [BNNGF-86661]
- Buffer overflows no longer occur in the VPN log. [BNNGF-87645]
- When using a secondary authentication scheme, the username is now sent as expected. [BNNGF-87648]
- A regression has been fixed that caused IPSec tunnels to show reverse routing interface mismatch with the option Add VPN routes to main table routing enabled, depending on whether there were two overlapping destination networks. This affected IKEv2 with an additionally enabled option One VPN Tunnel per Subnet Pair, and IKEv1 in general, but in both cases only with the main table routing option enabled. [BNNGF-89076]
- IPsec tunnels using hostnames do not terminate anymore in certain situations. [BNNGF-89412]
- In the Listening IP Configuration section for the VPN service, switching between the options Device and Explicit now works as expected with the listener switching to the appropriate IP. [BNNGF-89480]
- VPN tunnels no longer cause unexpected loads. [BNNGF-89515]
- Azure vWAN tunnels do not terminate after a certain time in certain situations. [BNNGF-89672]
- TINA tunnels no longer terminate due to failing heartbeats. [BNNGF-89808]
- The traffic for the Teams application is now recognized correctly. [BNNGF-89834]
- Routed VPN no longer removes the VPN index and is now displayed on GTI as expected. [BNNGF-90098]
- PPPoE now works with TINA as expected. [BNNGF-90148]
- When operating a single VPN tunnel with the option 'One tunnel per subnet', all transports now work as expected after re-activating the tunnel. [BNNGF-90852]
- Routed VPN now uses VPN interfaces as expected. [BNNGF-91115]
- Routed VPN now works as expected if the VPN index is changed with GTI. [BNNGF-91572]
Known Issues
- Status LEDs do not work on the M40b USB LTE modem. [BNNGF-82685]
- Barracuda OS – If a QoS profile has been created and assigned to a physical interface, this profile will be automatically overwritten by the simple QoS band when performing an HA failover or deleting the VPN tunnel assigned to this physical interface. [BNNGF-90831]
- Barracuda OS – Special characters are not processed correctly when using the RADIUS authentication scheme. [BNNGF-90980]
- Barracuda OS – After updating to firmware 9.0.1, the guest ticketing no longer saves guest tickets. [BNNGF-93071]
- Barracuda OS – GRE tunnels are not properly working. [BNNGF-93215]
- Control Center – After updating a Control Center to 9.0.1 and rolling out users for OTP, no email is sent out. [BNNGF-92695]
- Firewall – Inspecting traffic for QUIC/UDP 443 is currently not supported. [BNNGF-74540]
- Firewall – Existing sessions do not get terminated correctly when the scheduling object no longer matches. [BNNGF-91568]
- Firewall – When creating a new custom network app with a few ports (e.g., 4 ports) and the IP of a fileserver, any port is open instead of the configured 4 ports. [BNNGF-92511]
- Firewall – Reconfiguring a WSG Bridge leads to a broken ARP negotiation. As a workaround, reboot your instance. [BNNGF-92703]
- SD-WAN – SD-WAN Default Policies are not migrated automatically from 8.3 to 9.0. Select "Restore Policy List from Default" in SD-WAN Default Policies if a ruleset before 9.0.1 was using policies. [BNNGF-92435]
- SSL-VPN and CudaLaunch – Shared folders containing spaces in the folder name are no longer accessible via CudaLaunch. As a workaround, replace spaces with %20 [BNNGS-3970]
- SSL-VPN – SSL VPN may be vulnerable to HTTP request smuggling. [BNNGF-80814]
- Telemetry – For managed firewalls note that settings displayed in the UI on the Control Center and the managed box can differ depending on the cluster and firmware version. [BNNGF-89044]
- VPN – Dynmesh tunnels do not get established when both sites are behind a NAT after updating to 9.0.0. [BNNGF-90377]
- VPN – Since the update to 9.0.1, MFA requests with Radius push notifications fail when the MFA request is not accepted within approx. 6 seconds. [BNNGF-92696]
- Firewall - App-Detection – Initially failing app detection or invalid TLS certificate due to large Client Hello
Certain browsers force the use of Kyber, a post-quantum key agreement algorithm, in TLS. In turn, the Client Hello gets unusually large and initially might cause app detection to fail or an invalid TLS certificate for TLS inspection. After a page refresh in the browser, the app is detected correctly and the TLS certificate is valid.
A workaround is to disable the flag "TLS 1.3 hybridized Kyber support" / X25519Kyber768 in Google Chrome (chrome://flags/), Microsoft Edge (edge://flags/), and "security.tls.enable_kyber" in Firefox (about:config).
For Google Chrome and Chrome OS there is also a policy that can alternatively be used to control this flag. See https://chromeenterprise.google/policies/#PostQuantumKeyAgreementEnabled. [BNNGF-93365]