Important Announcements and Notes
Outdated technical features are subject to removal to keep the CloudGen Firewall up to date and performing properly. See the following two paragraphs for the features that will be removed in this release and the features that are subject to removal in upcoming releases.
Certain features will be removed completely because they have become technically obsolete; other features have become outdated and will be replaced by improved technology.
Operators of Firewall Models F800 and F900
Features No Longer Supported as of the 8.3.2 Release
Virus Scanning with ClamAV
The firewall will start the service, however, the service will be highlighted with a warning notifying the customer about the deprecation.
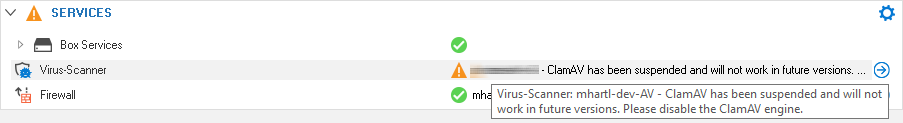
Features that Will Become Obsolete in an Upcoming Release
FWAudit
WAN Optimization
CloudGen Firewall Web UI
PKI
Reset SMS Counter
SMS Control
Precautionary Security Measures for Control Centers
Use the Appropriate Firewall Admin Release
Generally, Barracuda Networks recommends using the latest version of Firewall Admin for a new firmware release.
As of the public availability of this firmware 8.3.2, Barracuda Networks recommends using at least Firewall Admin version 8.3.2-xx. You can download this version here: https://dlportal.barracudanetworks.com/#/packages/5651/FirewallAdmin_8.3.2-84.exe
Release Notes
Firmware version 8.3.2 is a minor release.
EoL and EoS Status
For more information on which devices and services have reached Eol or EoS status, see the following:
What's New in Version 8.3.2
ConfTemplates Improvements
The configuration templates have been improved and include multiple new ConfTemplate units. These new ConfTemplate units now support among many others configuring networks, routes, VLANs, or authentication.
Also, a new pool object has been created to support the automated allocation of VIPs and MIPs in conjunction with ConfTemplates.
For more information, see Configuration Templates.
Improvements Included in Version 8.3.2
Authentication
The mail template in the TOTP Bulk Enrollment settings can be changed as expected. [BNNGF-81664]
The maximum timeout for TACACS+ has been increased to 45 seconds. [BNNGF-82350]
It is now possible to preselect an authentication scheme for CC Template Admins. [BNNGF-83910]
The validation of certificates no longer causes issues in certain situations. [BNNGF-88317]
DC Agent timeouts now work as expected on subsequent logins. [BNNGF-84267]
Authentication sync now works as expected. [BNNGF-84440]
The IKEv2 RADIUS authentication now works as expected with user info helper schemes enabled. [BNNGF-84571]
When group caching is enabled, authentication via MSAD now works as expected. [BNNGF-87091]
Barracuda OS
DHCP relay now uses the correct type of IP address and works as expected. [BNNGF-71929]
The bond interface no longer changes to interface 'e1' and the config for the secondary box can now be activated. [BNNGF-75351]
MSAD traffic will no longer be detected as BitTorrent. [BNNGF-75606]
The BFD process now continues running and no longer restarts when BFD settings are updated on the fly. [BNNGF-76921]
The integrity check logic now works as expected if a default route via shared IP is configured. [BNNGF-78794]
The bridge no longer stops working unexpectedly in certain situations. [BNNGF-78802]
Changing into the 'home directory' no longer causes permission errors. [BNNGF-81081]
SNMP no longer crashes in certain situations. [BNNGF-81130]
Login events no longer cause firewall rules to fail in certain situations. [BNNGF-82853]
Mounting the CIFS file system now works as expected. [BNNGF-83182]
The IPv6 auto-configuration no longer causes issues in certain situations. [BNNGF-83906]
Cooking statistics no longer cause issues in certain situations. [BNNGF-84065]
The
bsnmdno longer consumes available CPU time in certain situations. [BNNGF-84173]The
systemdno longer causes spikes every 10 seconds. [BNNGF-84674]The number of routes within a source-based table no longer flaps between 0 and another value. [BNNGF-84844]
The GUI-to-text is now updated if the text-based config is disabled and the user interface config is used. [BNNGF-84845]
The firewall no longer crashes in certain situations. [BNNGF-84847]
Hotfixes that are included in other hotfixes are now also visible at DASHBOARD > UPDATES > Installed as expected. [BNNGF-85235]
SNMP errors no longer flood the log and are now handled as 'information'. [BNNGF-85479]
SNMPv3 is no longer blocked by the default ruleset. [BNNGF-85811]
OSPF routes are now introduced at the configured routing table. [BNNGF-85986]
After a network activation, the OSPF routing table is now in place as expected. [BNNGF-85987]
If a new route is learned on one daemon and already exists in the system, it will now be replaced with a new route of a favorable metric. [BNNGF-87041]
The Network activation required dialog no longer shows up after a site-specific network is edited. [BNNGF-87084]
The Barracuda Reporting Server daemon now increases the time between retries if the connection can't be established. [BNNGF-87177]
The access control service no longer causes restart loops. [BNNGF-87475]
The creation of a system report now works as expected. [BNNGF-87497]
Firewalls no longer send data if Firewall Insights does not respond. [BNNGF-87850]
Source base thrown boot routes are no longer removed with a soft activation. [BNNGF-87926]
IPMI logs no longer show errors after updating the IPMI firmware. [BNNGF-88127]
As Mexico no longer has daylight-saving time, the correct time is set for America/Mexico City. [BNNGF-89326]
The configuration of custom IPFIX templates now works as expected. [BNNGF-89327]
The provider name for WiFi is now handled as expected. [BNNGF-90954]
ConfTemplates
After creating an SC box with ConfTemplates, the SC firmware update over CC now works as expected. [BNNGF-88646]
Control Center
When a vendor ID is converted from IP to hexadecimal, the colon character is no longer appended to the end of the string. [BNNGF-76967]
The clone box wizard now works with multiple default routes as expected. [BNNGF-80736]
The edit fields Naming Replace From and Naming Replace To have been added to the Clone Box Wizard to move a service from a box in a certain cluster to a box in another cluster. [BNNGF-81362]
Information about firmware updates for managed boxes is now updated correctly on Control Centers with firmware 8.2.1. [BNNGF-82938]
CC admin now configures firewall rules as expected. [BNNGF-83248]
RCS now shows changes from external LDAP admins as expected. [BNNGF-83186]
Range-level CC admins can now kill the session of other range admins as expected. [BNNGF-84843]
When trying to determine the boxes in a cluster, the related REST call no longer runs into any issues. [BNNGF-84899]
Changing the CC Admin password now works as expected. [BNNGF-85237]
IPS pattern updates now work as expected on HA firewalls. [BNNGF-85478]
Dummy changes for the Box Properties node and the IPS configuration node no longer occur in certain situations. [BNNGF-86917]
Boxes now show up correctly on the Status Map. [BNNGF-87058]
In case of a pool license being used only for one firewall of a high availability cluster, the pool license is now only assigned to that single HA partner in case of a license update. [BNNGF-87476]
The Status Map no longer shows firewalls after their removal in the configuration tree. [BNNGF-88275]
When an HA box is deleted, it is now properly removed from the internal database. [BNNGF-88755]
The CC Status tab in Barracuda Firewall Admin no longer crashes in certain situations. [BNNGF-89278]
FQDNs are now allowed to be entered for the syslog destination. [BNNGF-89405]
DHCP
DHCP service sends Dynamic DNS updates in Simple Mode. [BNNGF-83023]
A new option with the name 'standard' has been added to the menu list for DNS Update Scheme at CONFIGURATION > Configuration Tree > Assigned Services > DHCP Enterprise Configuration > Address Pools > DNS Update Configuration. [BNNGF-83041]
Firewall
The Firewall Live view shows traffic throughput as expected. [BNNGF-79451]
Salesforce traffic is now recognized correctly. [BNNGF-83185]
The setting for SSL Inspection no longer displays the wrong status if the configuration is set to Auto in the security policy. [BNNGF-83584]
F-Secure AV updates are now correctly detected as what they are. [BNNGF-83908]
The Swish FTP client is now correctly detected. [BNNGF-83909]
Offline authentication no longer times out. [BNNGF-84035]
A backslash in a username is now correctly evaluated in a rule set and sessions are therefore no longer blocked. [BNNGF-84163]
The firewall no longer crashes during TFTP file transfers in certain situations. [BNNGF-84256]
Applications are now blocked as expected. [BNNGF-84432]
SD-WAN policy profiles now support creating policies using a protocol/port combination. [BNNGF-84524]
When using Offline Firewall Authentication, the correct page logo is now displayed. [BNNGF-84564]
Protocol matching now works with policies as expected. [BNNGF-85031]
Offline authentication no longer times out. [BNNGF-85166]
Traffic shaping uses the outbound rate limit instead of the inbound rate limit for inbound traffic with PRX and IPRX sessions. This affects SSL/TLS inspection, AV scanning, and Generic TCP Proxy. [BNNGF-85241]
SNAT now works as expected for an HA partner in a CloudGen WAN setup. [BNNGF-85379]
The firewall no longer crashes when applying URL categorization to IPv6 traffic. [BNNGF-85473]
Link protection has been improved for HTML emails with links that contain line breaks. [BNNGF-85474]
The device filter Any Interface now works as expected in FIREWALL > Live. [BNNGF-85689]
In very rare cases, data was not sent to the FW activity log. [BNNGF-85755]
DST NAT now handles all entries for redirection as expected. [BNNGF-85904]
Correctly enabled dynamic rules in a c-firewall's local and special ruleset now match as expected. [BNNGF-86072]
Traffic to an SQL server is now forwarded as expected. [BNNGF-86077]
DST NAT and policies no longer cause erroneous app-ruleset evaluation. [BNNGF-86080]
The firewall no longer crashes on LOUT if webmsg-syslog traffic is being shaped. [BNNGF-86134]
Sporadic crashes with application detection no longer occur in certain situations. [BNNGF-86561]
Traffic shaping no longer causes the firewall to stall into a soft lock of all CPUs. [BNNGF-86654]
Team Viewer version 15 is now blocked if an application rule is set on the Firewall for the fixed version. [BNNGF-87108]
The system is no longer deadlocked on memory in certain situations. [BNNGF-87817]
The firewall no longer experiences memory leaks in certain situations. [BNNGF-87842]
The firewall now handles ONCRPC packets correctly and works as expected. [BNNGF-87935]
The TLSv1.1 is not used anymore if Restrict Strong Ciphers Only is chosen. [BNNGF-87939]
The firewall log no longer contains messages like "App Connect Socket received invalid len=44". [BNNGF-87941]
URLcat now works as expected with ports other than https 443. [BNNGF-88028]
Traffic redirected to destination 0.0.0.0/0 will never be sink-holed. [BNNGF-88289]
The Schedule firewall object works as expected. [BNNGF-88562]
In CONTROL > Network, all routes are now displayed as expected if the VPN service is active. [BNNGF-89308]
Firewall Admin
For compatibility reasons, it is no longer possible to open a DNS 7.x node in Firewall Admin 9.0. Firewall Admin 9.0 will display an appropriate notification in a window. [BNNGF-77636]
When bulk-assigning licenses, HA clusters are now shown as 1 unit, and the count numbers are now calculated correctly. [BNNGF-83190]
The view of CONTROL > Network now builds up with the expected standard speed and no longer causes long loading times with active BGP. [BNNGF-84037]
CC administrators with an 'operator' role are now allowed to create par files and push configurations to Zero Touch. [BNNGF-84058]
It is now possible to copy messages from the notification area in Firewall Admin. [BNNGF-84282]
Labels for site-to-site QoS policies have been equalized in Barracuda Firewall Admin. [BNNGF-84322], [BNNGF-84622]
When starting the GTI editor the first time, there is now an empty group present, and all services are displayed. [BNNGF-84625]
The column Output IF in Firewall Admin > Firewall History, now displays correct values. [BNNGF-84626]
App objects are now allowed in all policies. [BNNGF-84734]
The Remote Networks list in the VPN site-to-site tunnel configuration list now displays correct netmasks. [BNNGF-84745]
Barracuda Firewall Admin no longer crashes in certain situations. [BNNGF-84792]
The Access Control Service no longer crashes in certain situations. [BNNGF-87583]
Copying an IP address from a firewall rule using the Copy <IP> to Clipboard feature and applying it as a filter in the Firewall View (live or history) now works as expected. [BNNGF-88674]
Barracuda Firewall Admin no longer crashes under high latency and high system load. [BNNGF-88735]
Google Cloud
When deploying a new CGF in the Google Cloud, SSH public keys are set considering both the Google standard for project-wide SSH keys and individual custom keys. [BNNGF-88599]
HTTP-Proxy
The HTTP proxy now starts successfully after a failover even if SSL Inspection is enabled and if there are duplicate sub-domains configured for exclusion. [BNNGF-80253]
The reverse proxy exchange authentication now works as expected. [BNNGF-81512]
The traffic throughput of the reverse proxy now works as expected after a firmware update. [BNNGF-84038]
The HTTP Proxy now handles large POST requests as expected. [BNNGF-87087]
REST
Barracuda Networks' OpenAPI specification now works as expected with OpenAPI clients/generators. [BNNGF-87466]
The REST API queries now work as expected for LDAP and MSAD. [BNNGF-87508]
A configuration change on a firewall rulest via REST now correctly adapts the ruleset ID. [BNNGF-88263]
Virus Scanner
The AV service no longer shows erroneous warnings in certain situations. [BNNGF-84301]
Scanned ATP files are removed as expected. [BNNGF-85957]
VPN
Strongswan will be activated only upon a configuration change and only if IKEv2 site-to-site OR/AND client-to-site are configured. [BNNGF-52334]
If HA Tunnel Sync is enabled in CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN > VPN Settings, a VPN tunnel now works as expected when an HA failover is initiated. [BNNGF-54419]
Configured IKEv1 routes will no longer be introduced into the main routing table, but rather be handled as source routes. [BNNGF-78903]
A rare cause for an issue with loss of all VPN tunnels for a GTI configuration has been fixed where the option Dedicated Secondary Config was active in Properties > Operational, triggered by box network configuration changes. This only affected box server setups. [BNNGF-83380]
When IKEv2 uses RADIUS for authentication, it now uses the timeout values from the authentication service. [BNNGF-84576]
SC networks are now introduced into VPN table 5 as expected. [BNNGF-84737]
VPN tunnels no longer flap during rekeying. [BNNGF-85519]
Memory issues no longer occur if a bulk transport is configured as a routing transport. [BNNGF-86074]
The QoS band is now shown in the Live View as expected. [BNNGF-86661]
A regression has been fixed that caused IPSec tunnels to show reverse routing interface mismatch with the option Add VPN routes to main table routing enabled, depending on whether there were two overlapping destination networks. This affected IKEv2 with an additionally enabled option One VPN Tunnel per Subnet Pair, and IKEv1 in general, in both cases only with the main table routing option enabled. [BNNGF-89076]
In the Listening IP Configuration section for the VPN service, switching between the options Device and Explicit now works as expected with the listener switching to the appropriate IP. [BNNGF-89480]
Known Issues
Known Issues Related to CGF Policy Profiles
IMPORTANT – Policy profiles cannot be used on a VPN concentrator or Secure Access Controller!
Firewall – If a VPN TINA tunnel transport over a specific ISP goes down, the Internet traffic over the same ISP link will not work either. [BNNGF-81749]
Provider class in boxnet must not be changed "afterward" unless existing VPN tunnels are reconfigured accordingly.
There is currently no VRF support for policies in 8.3.2.
Known Issues Related to Other Topics
Currently, no RCS information is logged for Named Networks. [BNNGF-47097]
The learn-only mode for OSPF is not working as expected. [BNNGF-65299]
Firewall – Inspecting traffic for QUIC / UDP 443 is currently not supported. [BNNGF-74540]
Firewall – SSL inspection breaks on Office 365 admin page with TLS 1.3. [BNNGF-83026]
NOTE: If a contacted server does not support at least the configured minimum TLS version, then no connections to that server will be possible. Connections will be reset. This can especially have an impact on embedded frames or Cross-Origin Resource Sharing (CORS) when those servers do not support the same TLS version as the main site.
For troubleshooting:
Turn Box > Infrastructure Services > General Firewall Configuration > Advanced Log Settings > SSL/TLS loglevel to debug.
Look out for "alert protocol version" in SSL logs (Assigned Services > NGFW > SSL), e.g.:11.04.2022 15:36:46 Info firewall: [TAP3Worker] Worker 1: Session 1271: SSL handshake to server failed: ID 2400 192.168.100.95:54525 <=> 104.103.84.247:443 assets.onestore.ms: error in OpenSSL library:error:0A00042E:SSLroutines::tlsv1 alert protocol versionFirewall – The synflood protection value Server-Default is not working as expected. [BNNGF-91455]
Barracuda OS – The authentication service
phibsdoes not start after updating to version 8.3.2. [BNNGF-90848]
As a workaround, restart the firewall after updating to version 8.3.2.CudaLaunch – After upgrading your iOS device to iOS 17, it is not possible to connect with CudaLaunch to RDP resources. [BNNGS-3975]
