Some network environments require additional security levels to authenticate users when they access specific high-risk VPN or SSL VPN resources. For an additional level of security, multi-factor authentication can be enabled for accounts on an individual basis, using a Time-based One-time Password (TOTP) as a secondary authentication method. The Barracuda CloudGen Firewall supports multi-factor authentication for client-to-site VPN (TINA protocol only), SSL VPN, CudaLaunch, and the Barracuda VPN Client for Windows, macOS, and Linux. Time-based One-time Password authentication is not supported on iOS devices. Multi-Factor Authentication using TOTP requires an Advanced Remote Access subscription. For more information, see Subscriptions.
Before You Begin
- Configure a primary authentication scheme, for example, MSAD. For more information, see How to Configure MSAD Authentication.
- In the Authentication Service > Timeouts and Logging configuration, set the Request Timeout to
30. For more information, see How to Configure Authentication Service Timeouts and Logging.
- In the Authentication Service > Timeouts and Logging configuration, set the Request Timeout to
If you bulk enroll more than 20 users, you must temporarily increase the Configuration Read Timeout:
- In Firewall Admin, click the hamburger menu on the top left and select Settings.
- Click Client Settings.
- In the Connectivity Options section, set Configuration Read Timeout to six times the number of users in seconds. For example, for 500 users, enter
30000. - Restart Firewall Admin.
- In Firewall Admin, click the hamburger menu on the top left and select Settings.
- If you bulk enroll, you must also set up a mail server so that the enrollment emails get sent out.
Step 1. Enable Time-based OTP Authentication
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Authentication Service.
- In the left navigation pane, select TOTP Authentication.
- Click Lock.
- Enable Time-based OTP as authentication scheme.
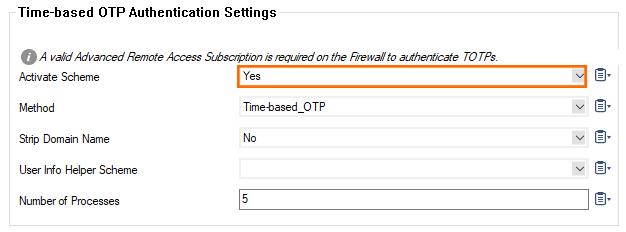
- (optional) To let users log in with domain and username (e.g., user@domain.com or domain/user), set Strip Domain Name to Yes.
- If group information is queried from a different authentication scheme, select the scheme from the User Info Helper Scheme list. For example, select LDAP if group information must be queried from an LDAP directory.
Click Send Changes and Activate.
Step 2. Enroll Users and Groups
The Barracuda CloudGen Firewall provides two options to enroll users and groups for TOTP authentication:
- Bulk Enrollment – Automatically enroll a group of users, e.g., from your authentication server.
- Self Enrollment – Configure self-enrollment for users to set up Time-based OTP. This option is available for the SSL VPN web portal, CudaLaunch, and the TOTP web portal.
Bulk Enrollment
Step 2.1. (optional) Export Users from Active Directory
To simplify the TOTP enrollment procedure for MSAD users, export the users as a comma-separated list from Active Directory to Excel and then to a .csv file. While exporting the users, define the required fields to get the format: [user]|[empty_password]|,[email]|.
- On the PowerShell, type the command:
Get-ADUser -SearchBase "OU= (your users),DC= (your domain)" -Filter * -properties mail | Format-Table -autosize -Property SamAccountName, mail > C:\bat\test.csv
Get-ADUser -SearchBase "OU=EU Users,DC=eu,DC=ad,DC=cuda-inc,DC=com" -Filter * -properties mail | Format-Table -autosize -Property SamAccountName, mail > C:\bat\test.csv
- Export the output to an Excel file.
- Add a column for
[empty_password] - Export the list into a .csv file.
You can now copy and paste the data from the .csv file into the Time-based OTP Bulk Enrollment configuration. Make sure to use the format: [username]|[password]|[email]|
Step 2.2. Enroll Users for TOTP Authentication
- Go to CONFIGURATION > Configuration Tree > Box > Infrastructure Services > Time-based OTP Bulk Enrollment.
- Click Lock.
- Add the users that should be enrolled for TOTP authentication:
- In the User Bulk Enrollment field, enter the users in the format
[username]|[password]|[email]|, or - Copy and paste the data from the .csv file with the users from your authentication server.
- In the User Bulk Enrollment field, enter the users in the format
Click Send Changes.
Click Import. The users are now listed in the Enrolled Users table.
Click Activate.
Managing Enrolled Users
All users that have been enrolled are listed in the Enrolled Users table. If you want to overwrite the entries using an updated list, select the Overwrite Users check box and re-import your users. To replace all enrolled users, select the Erase Users check box before adding new users. You can also revoke users that have already been enrolled. To prevent users from authenticating via TOTP, simply remove their details from the Enrolled Users list and activate the changes. Users that have been deleted will have to re-enroll themselves.
Self-Enrollment
When using the SSL VPN web portal, CudaLaunch, or the TOTP web portal, enable self-enrollment for users to set up Time-based OTP via the web interface.
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > SSL-VPN.
- Click Lock.
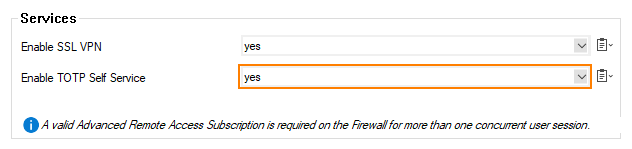
- Select yes to Enable the TOTP Self Service.
- In the left menu, click Time-based OTP.
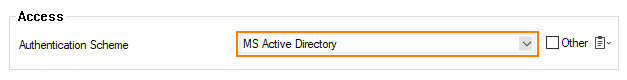
- From the Authentication Scheme drop-down list, select your authentication scheme. E.g., MS Active Directory.
- In the Self Enrollment section:
- Select yes to Enable Self Enrollment.
- In the Allowed User Groups field, add the users that should be allowed to self-enroll for TOTP authentication. Delete the asterisk and enter the MSAD group name. E.g.,
CN=sales - In the Blocked User Groups field, add the users that should be blocked from self-enrolling.
- (optional) Import your company Logo and customize the Login Message for your users.
Click Send Changes and Activate.
Users can now use the SSL VPN web portal, CudaLaunch, or go to the dedicated TOTP web portal (URL https://(IP of the SSL VPN service)/portal/totp.html) and enroll themselves for TOTP authentication. For more information, see How to Self-Enroll for Time-Based One-Time Passwords (TOTP) using the Simple TOTP Web Portal.
Step 3. Configure TOTP as Authentication Scheme
Enable TOTP authentication for client-to-site VPN, SSL VPN web portal, CudaLaunch, or the Barracuda VPN Client.
Enable TOTP for Client-to-Site VPN
Enable TOTP as the secondary authentication scheme:
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > Client to Site.
- Click Lock.
- Click the External CA tab and then click the Click here for options link. The Group VPN Settings window opens.
- Configure the settings for your VPN group. For more information, see How to Configure a Client-to-Site VPN Group Policy.
- From the Secondary Authentication Scheme drop-down list, select totp.
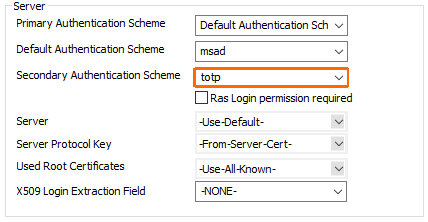
- Click OK.
- Click Send Changes and Activate.
Create a VPN group policy to enforce Time-based One-time Password (TOTP) authentication:
- Go to CONFIGURATION > Configuration Tree > Box > Assigned Services > VPN-Service > Client to Site.
- Click Lock.
- Click the External CA tab.
- Create or edit a group policy. For more information, see How to Configure a Client-to-Site VPN Group Policy.
- In the Edit Group Policy window, right-click the Group Policy Condition field and select New Rule.
- Configure the settings for your VPN group. For more information, see How to Configure a Client-to-Site VPN Group Policy.
- Select the Enable One-Time Password check box.
- Click OK.
- Click Send Changes and Activate.
Enable TOTP for SSL VPN and CudaLauch
To configure SSL VPN to use One-time Password authentication, create an Access Control Policy that requires TOTP authentication. For more information, see How to Configure Access Control Policies for One-Time Password Authentication and How to Self-Enroll for Time-Based One-Time Passwords (TOTP) using the Simple TOTP Web Portal.
Self-Enroll for TOTP
To enroll a mobile device using CudaLaunch or SSL VPN, install a TOTP-compatible app and complete the 2-step enrollment process to link the app with Time-based One-time Password Authentication on the CloudGen Firewall. For more information, see How to Self-Enroll for Time-Based One-Time Passwords (TOTP) Using CudaLaunch or the SSL VPN Web Portal.
Enable TOTP for the Barracuda VPN Client
To use TOTP on the Barracuda VPN Client, create or edit a VPN profile and enable One-time Password (OTP) extensions. For more information, see How to Create VPN Profiles.
