The more you understand threats, the better prepared you are to spot them. Review these one-page Threat Spotting Sheets to help your organization prevent these types of attacks.
Click a link to open the complimentary Threat Spotting Sheet PDF.
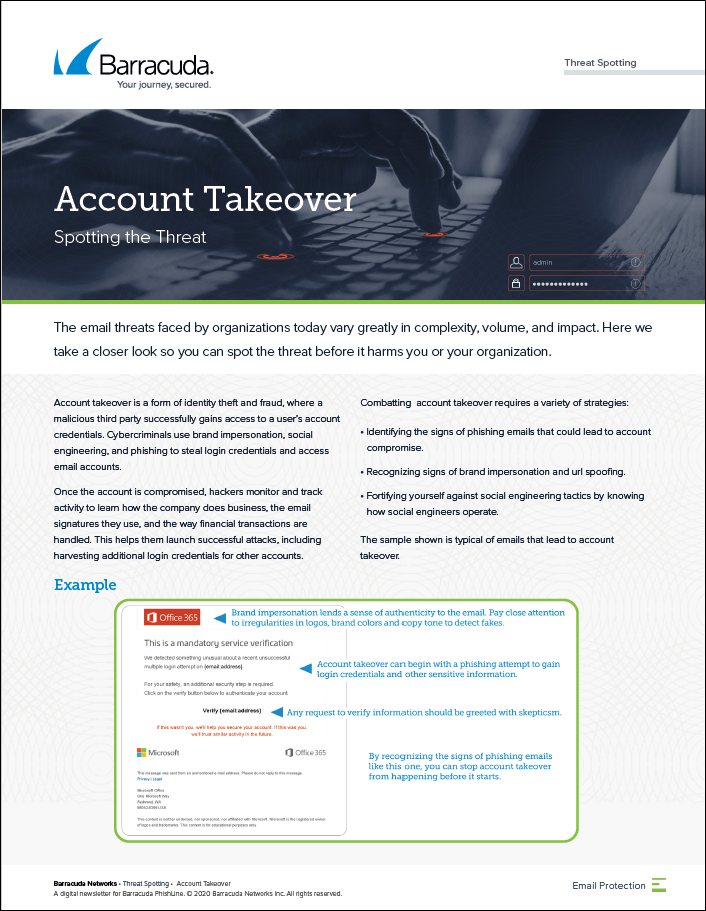
Account Takeover (ATO)
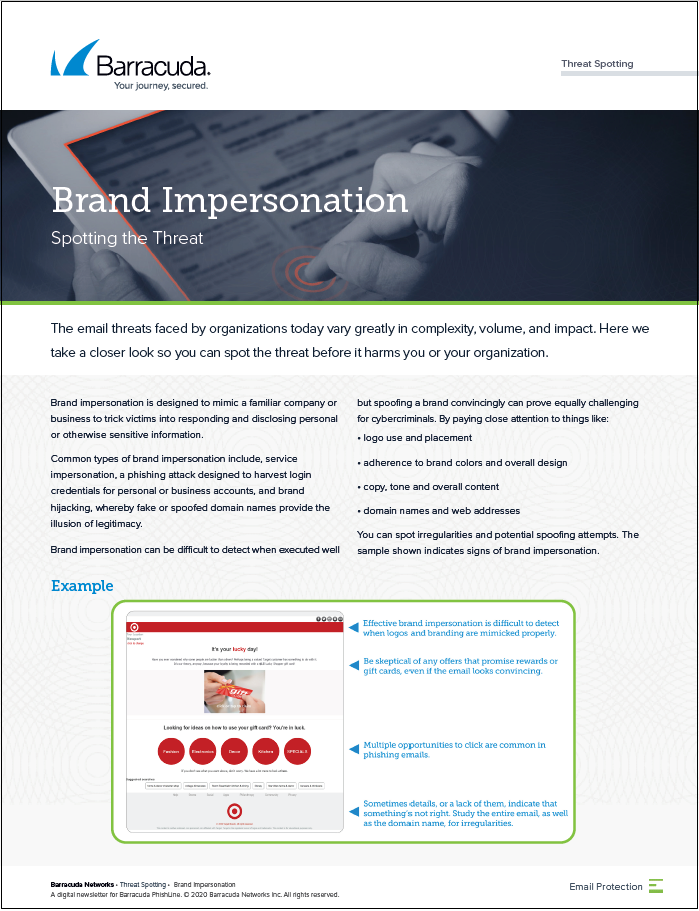
Brand Impersonation
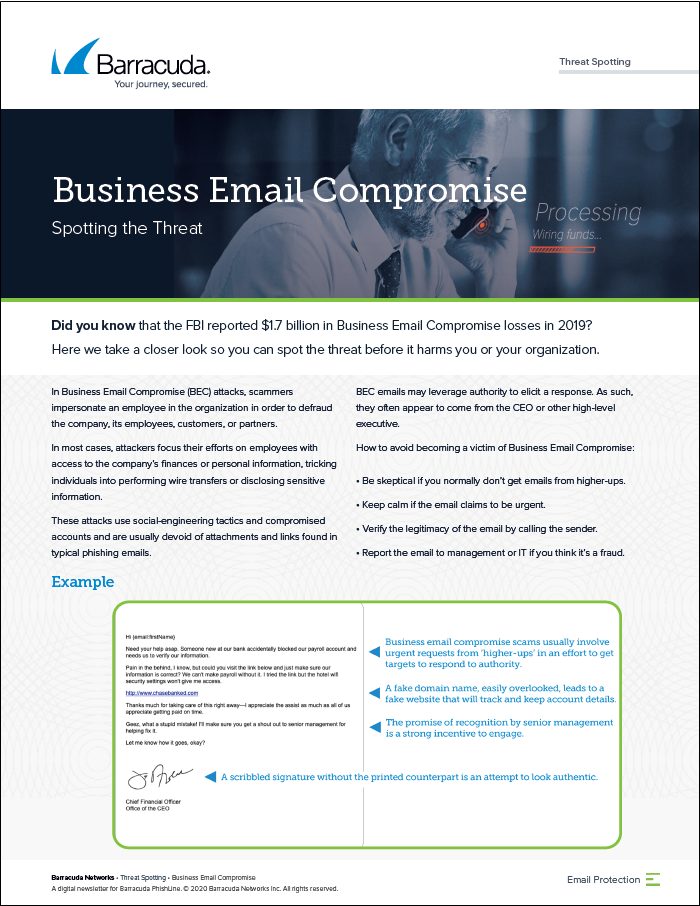
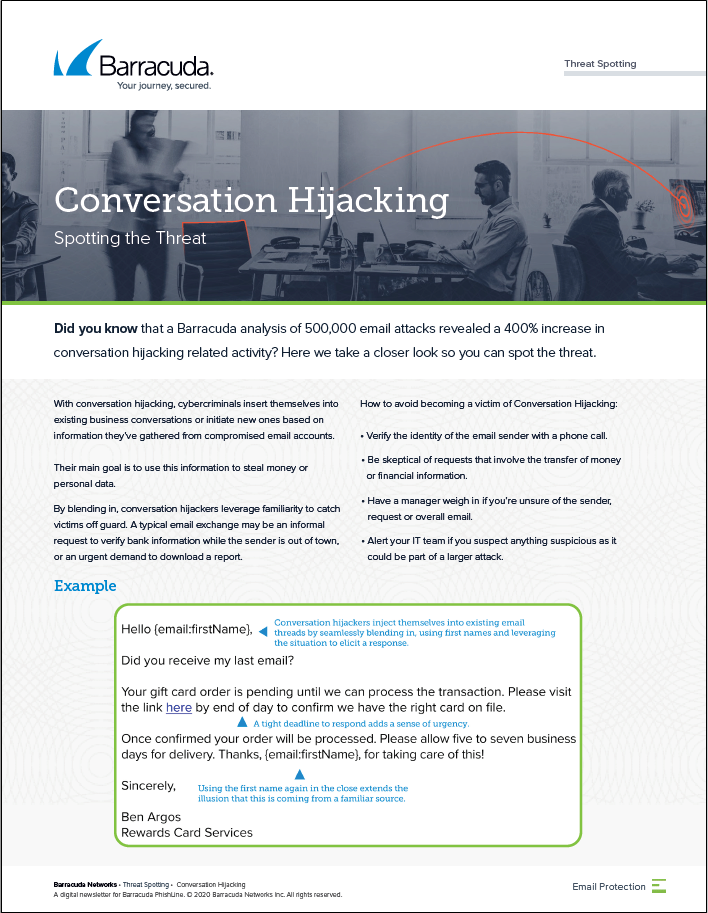
Business Email CompromiseConversation HijackingData Exfiltration
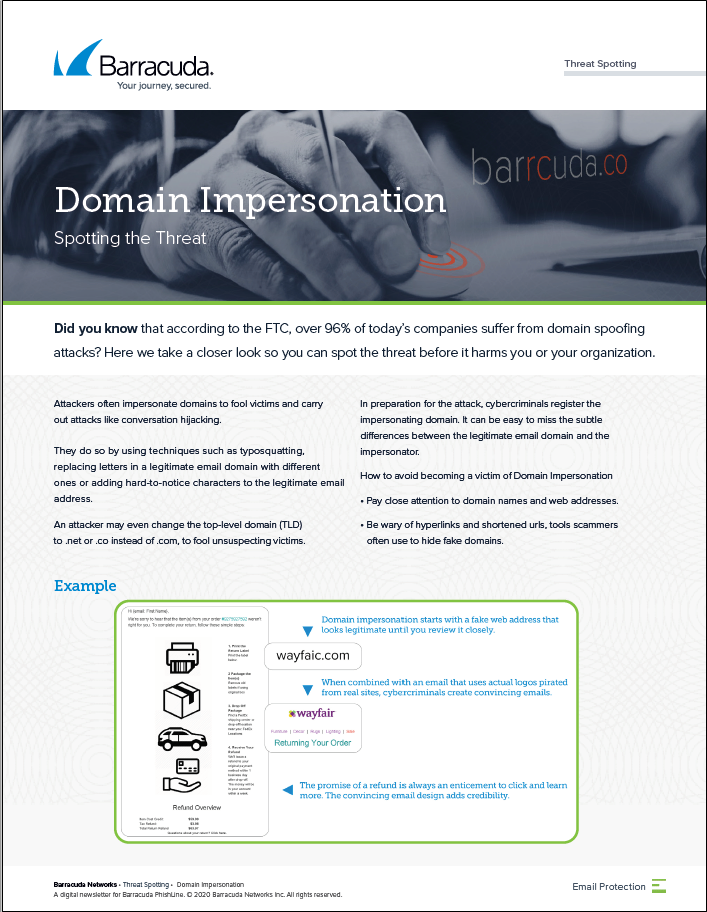
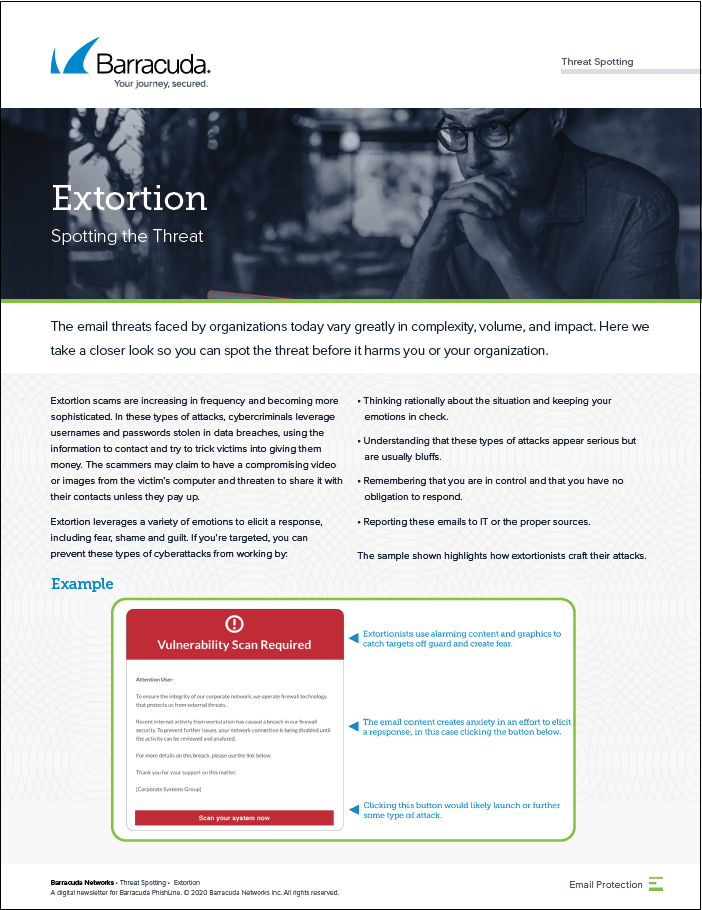
Domain ImpersonationExtortion
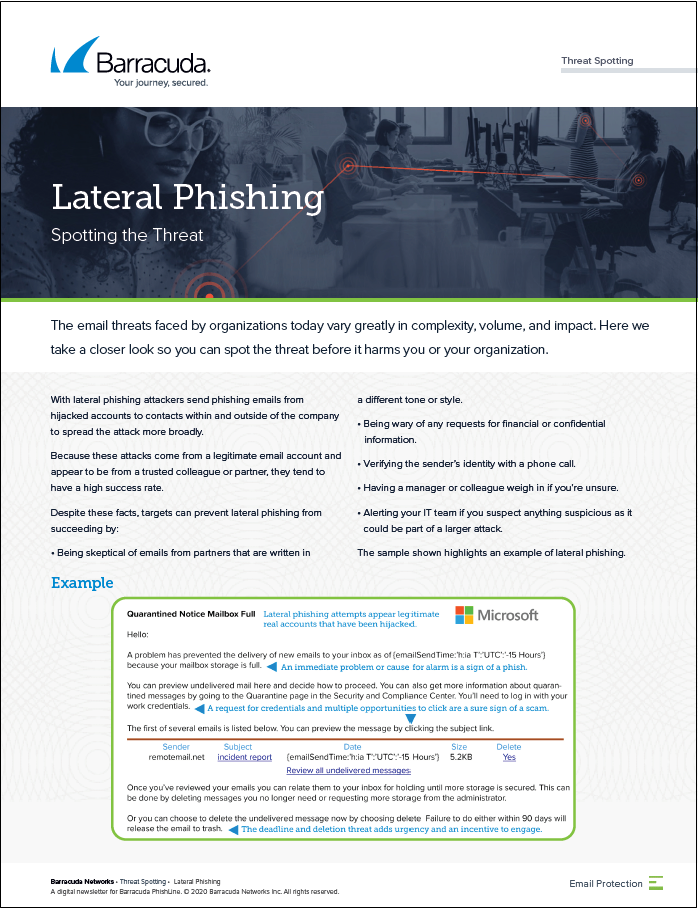
| Lateral Phishing
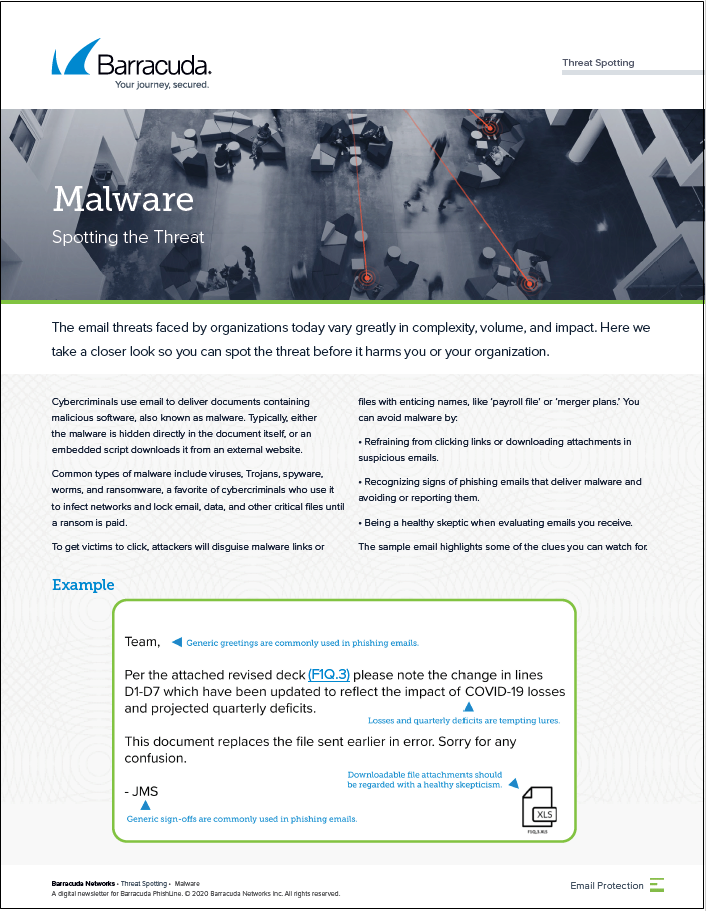
Malware
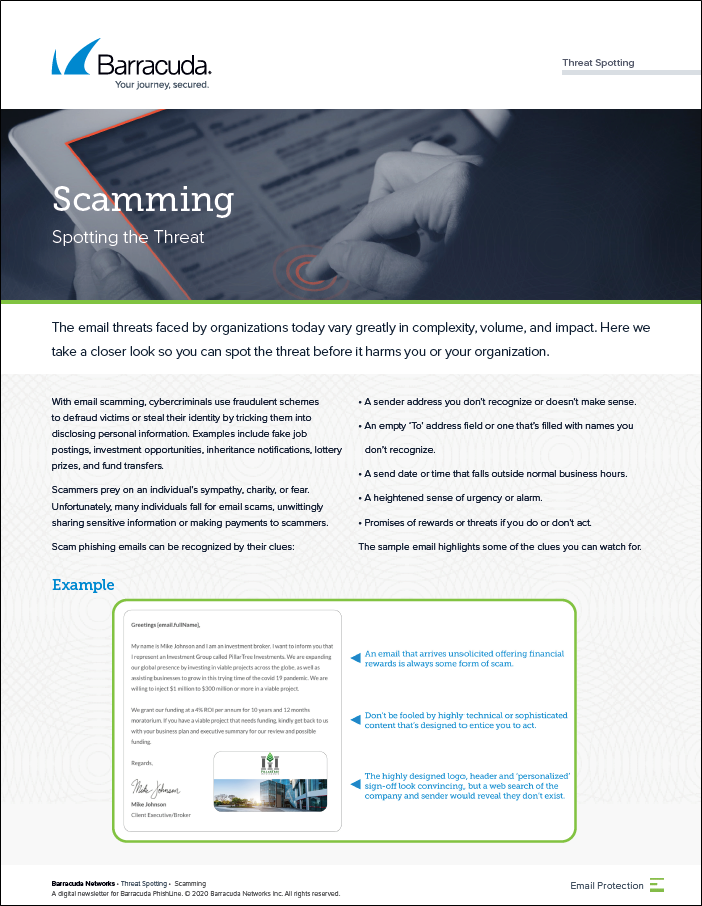
Scamming
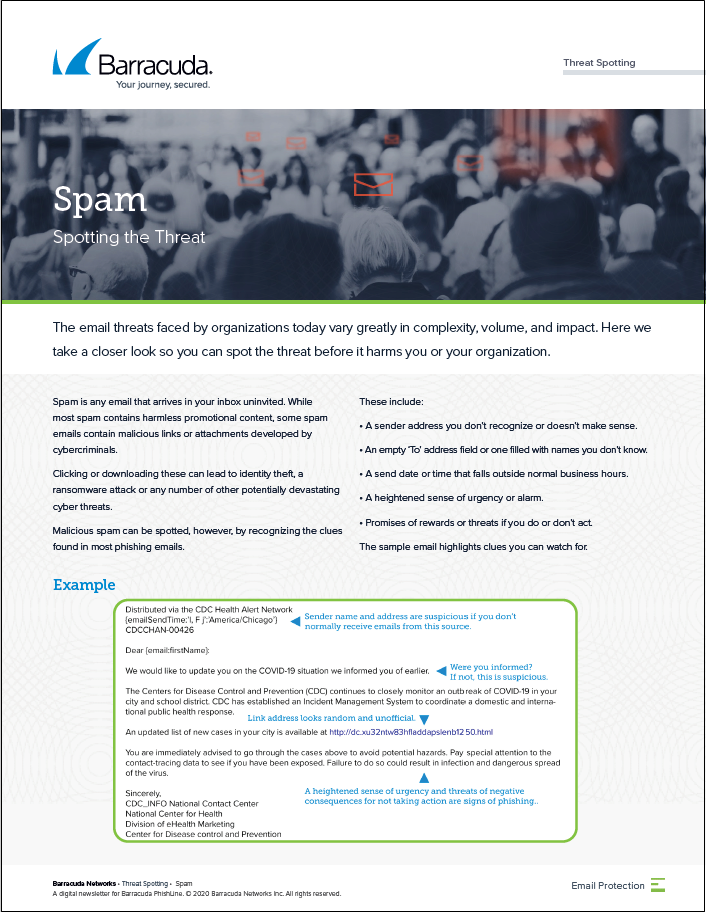
Spam
Spear Phishing
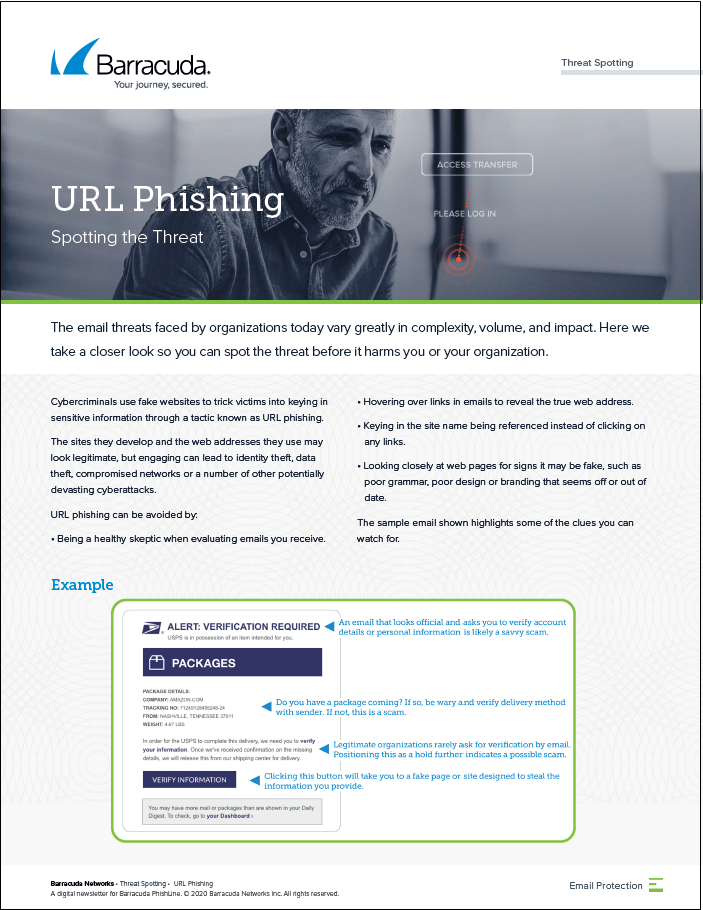
URL Phishing
|