One click on a malicious link is all it takes to unleash the worst the Internet has to offer. Click Thinking content encourages users to think before they act, providing helpful examples and insights that make training and learning fun. It also covers a wide range of information security topics relevant to today’s security-aware companies.
Click links on this page to download complimentary content.
Click Thinking – December 2025
Click Thinking – November 2025

Click Thinking – October 2025

Click Thinking – September 2025

Click Thinking – August 2025

Click Thinking – July 2025

Click Thinking – June 2025

Click Thinking – May 2025
Click Thinking – April 2025

Click Thinking – March 2025
Click Thinking – February 2025

Click Thinking – January 2025

Click Thinking – December 2024

Click Thinking – November 2024

Click Thinking – October 2024

Click Thinking – September 2024

Click Thinking – August 2024

Click Thinking – July 2024

Click Thinking – June 2024

Click Thinking – May 2024

Click Thinking – April 2024

Click Thinking – March 2024
Click Thinking – January-February 2024
Click Thinking – December 2023

Click Thinking – November 2023

Click Thinking – October 2023

Click Thinking – September 2023

Click Thinking – August 2023
Click Thinking – July 2023

Click Thinking – June 2023

Click Thinking – May 2023

Click Thinking – April 2023

Click Thinking – March 2023

Click Thinking – February 2023

Click Thinking – January 2023

Click Thinking – December 2022

Click Thinking – November 2022

Click Thinking – September 2022

Click Thinking – July 2022

Click Thinking – June 2022
![Social Media infographic[28].png](/resources/attachments/image/168560439/1/Social%20Media%20infographic%5B28%5D.png)
Click Thinking – May 2022
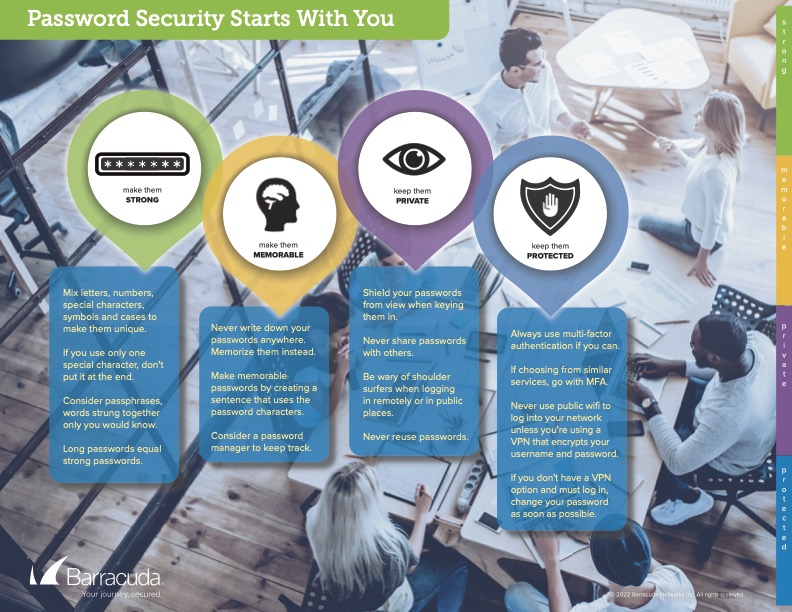
Click Thinking – April 2022
Click Thinking – February 2022

Click Thinking – January 2022

Click Thinking – December 2021

Click Thinking – November 2021

Click Thinking – October 2021

Click Thinking – Summer 2021

Click Thinking – May 2021
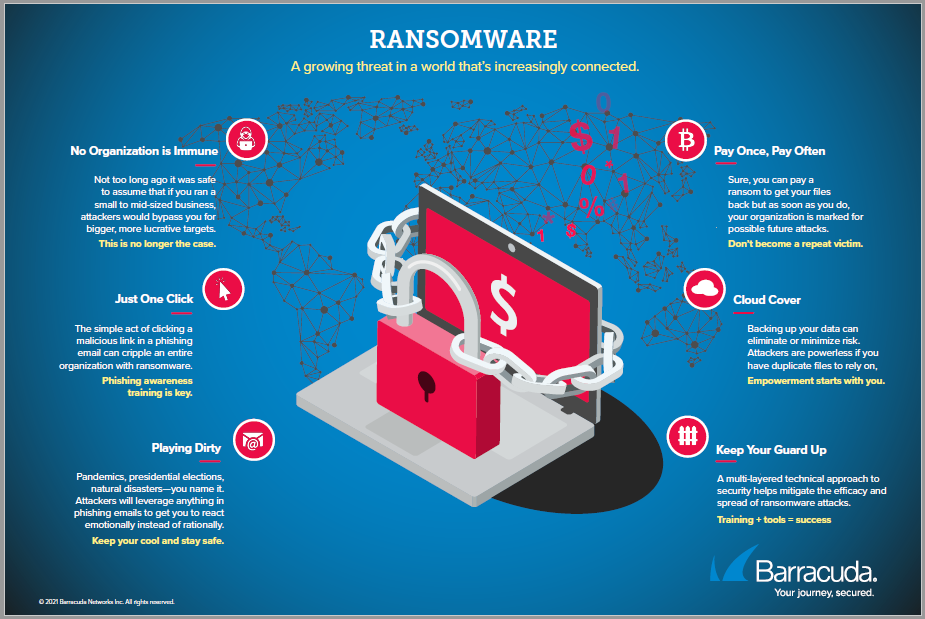
Click Thinking – April 2021

Click Thinking – March 2021

Click Thinking – February 2021

Click Thinking – January 2021
Click Thinking Bonus Feature: Fetch a Fish Game
Released November 2020

Fetch a Fish is an engaging way for your users to learn more about the 13 email threat types.
To find Fetch a Fish, log into Security Awareness Training. Navigate to Campaign > Click Thinking . Then use the filters in the left panel to search for Fetch.
Special Edition: Cyber Security Awareness Month Issue
Released October 2020

Email Threat Spotting Sheets (Separate article in Barracuda Campus)
Spam
Released September 2020

Account Takeover (ATO)
Released August 2020
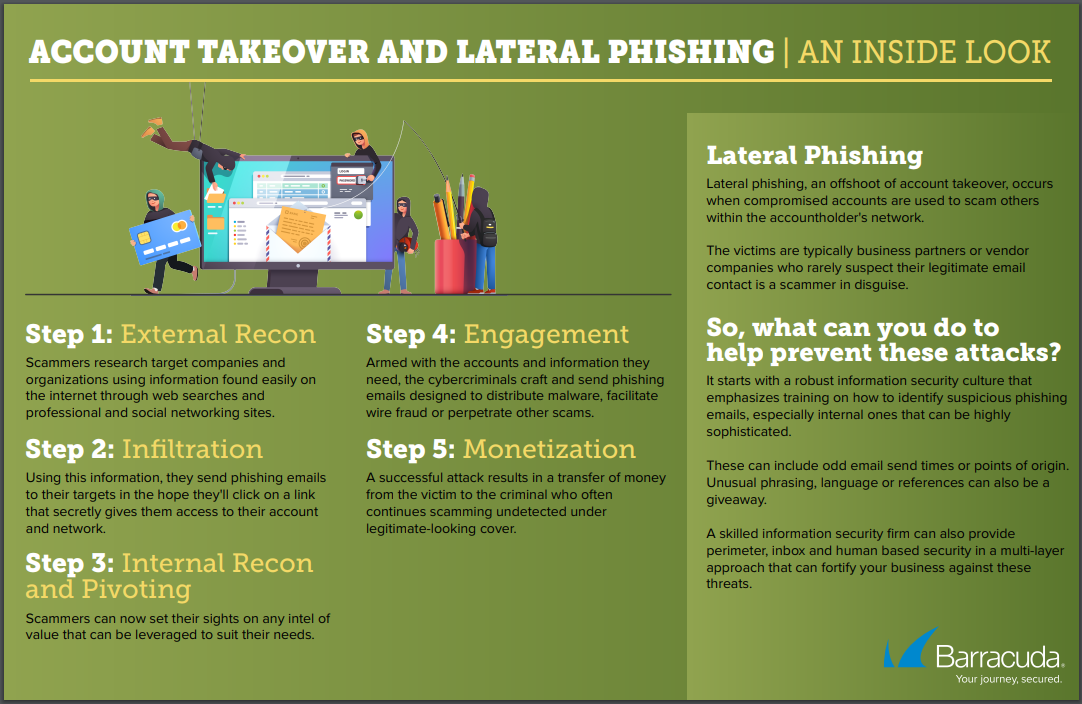
Staffing and Cybersecurity
Released June 2020
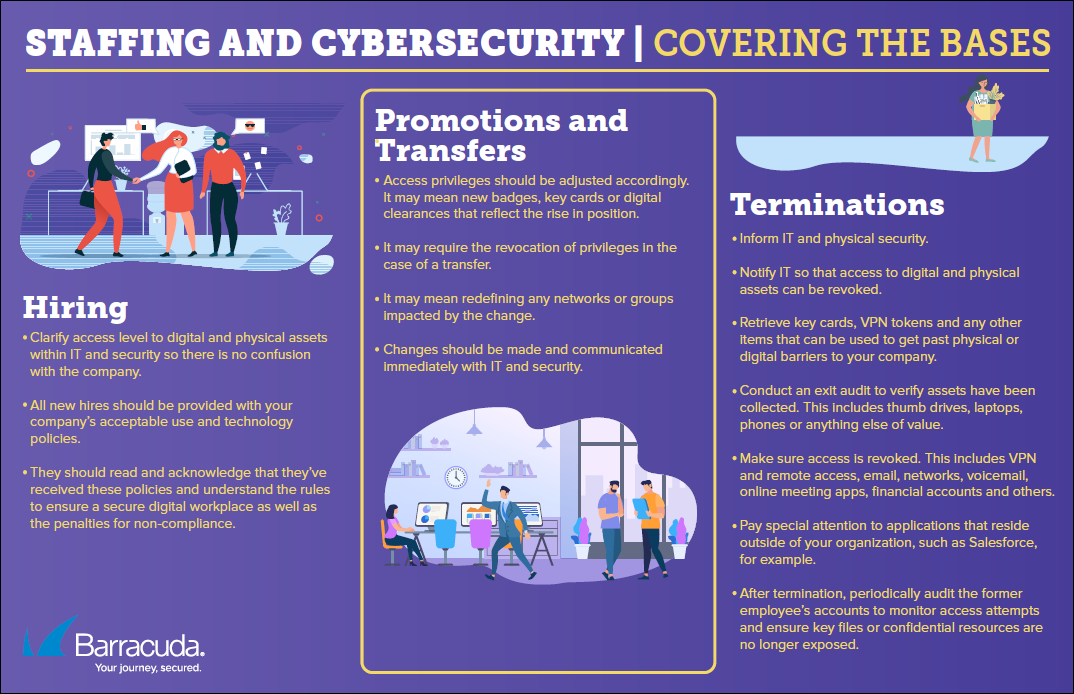
Access Control
Released May 2020

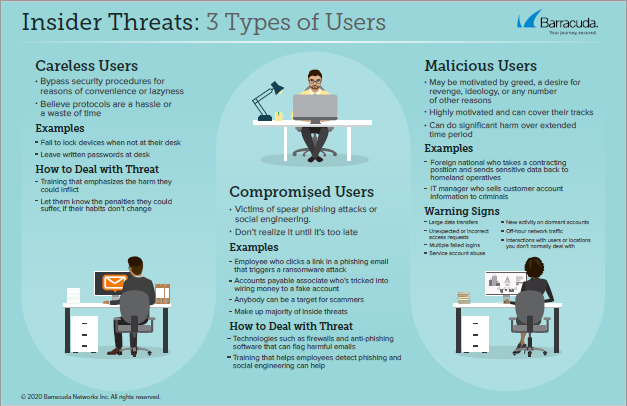
Insider Threat
Released April 2020
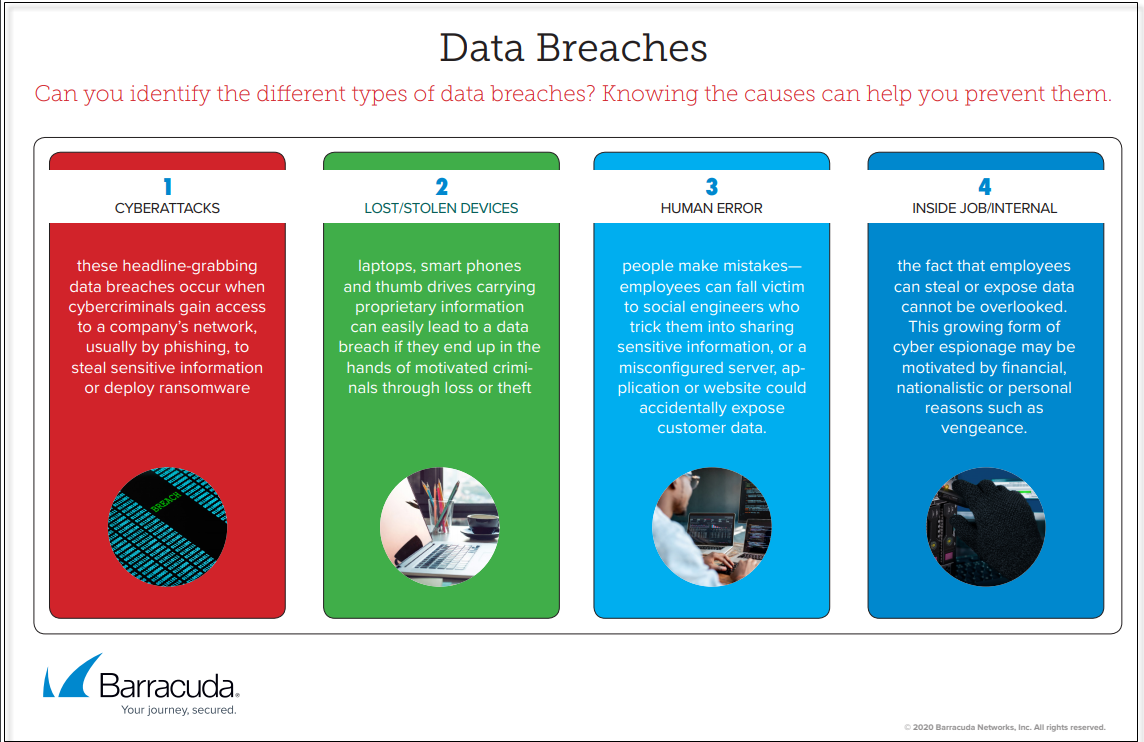
Data Breaches
Released March 2020
Bonus – COVID-19 – Working at Home
Re-released March 2020

Informs employees about safety while working from home. Especially helpful for those who are new to working from home due to COVID-19.
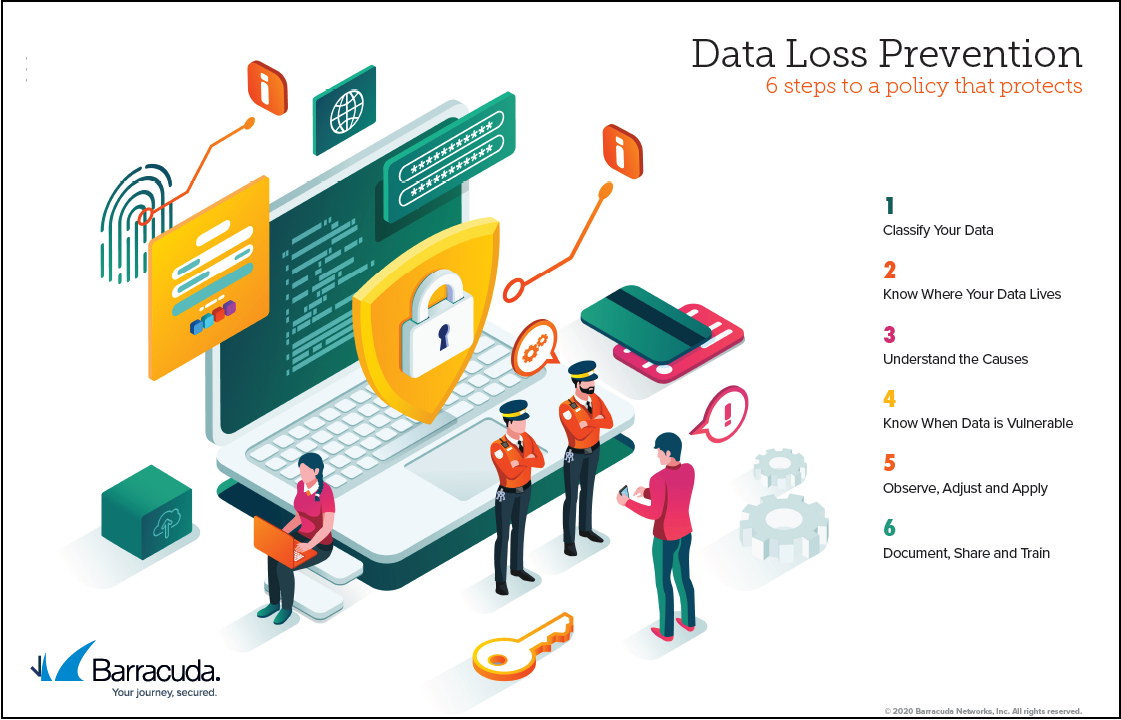
Data Loss Prevention
Released February 2020
Data Classification
Released January 2020

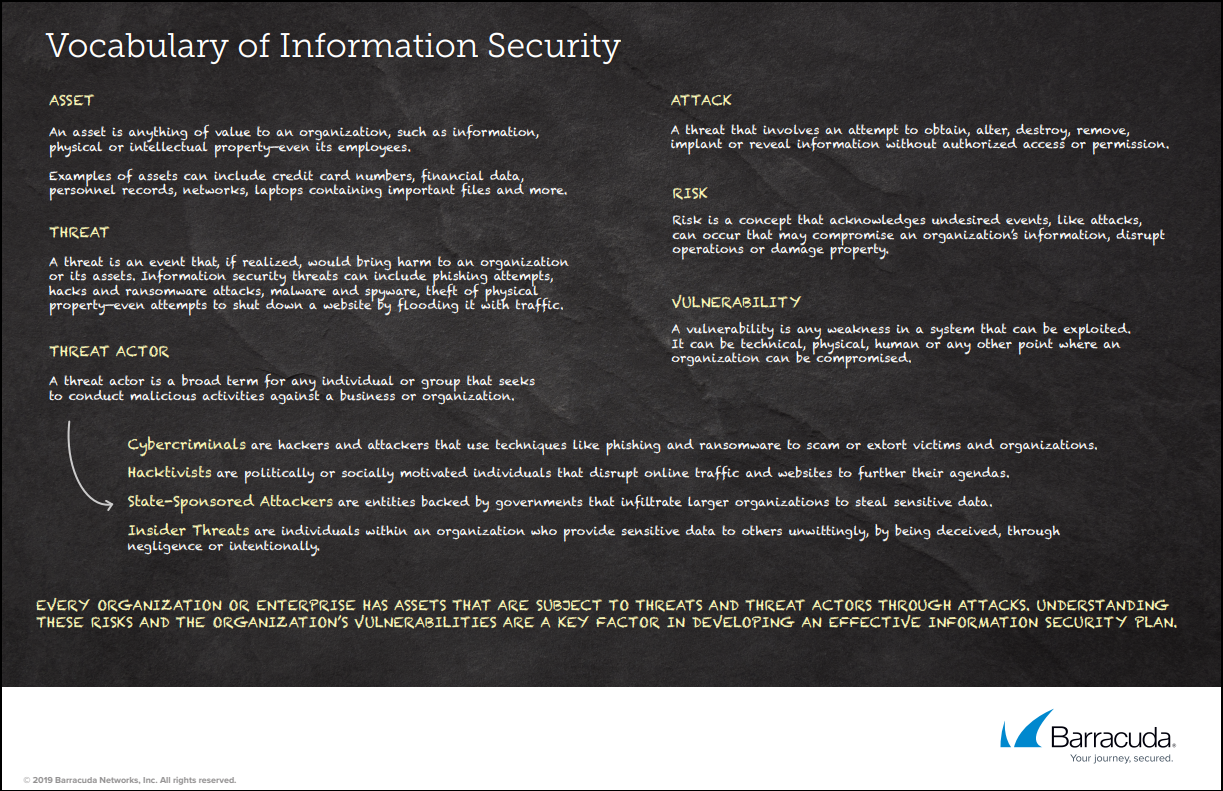
Vocabulary of Information Security
Released December 2019
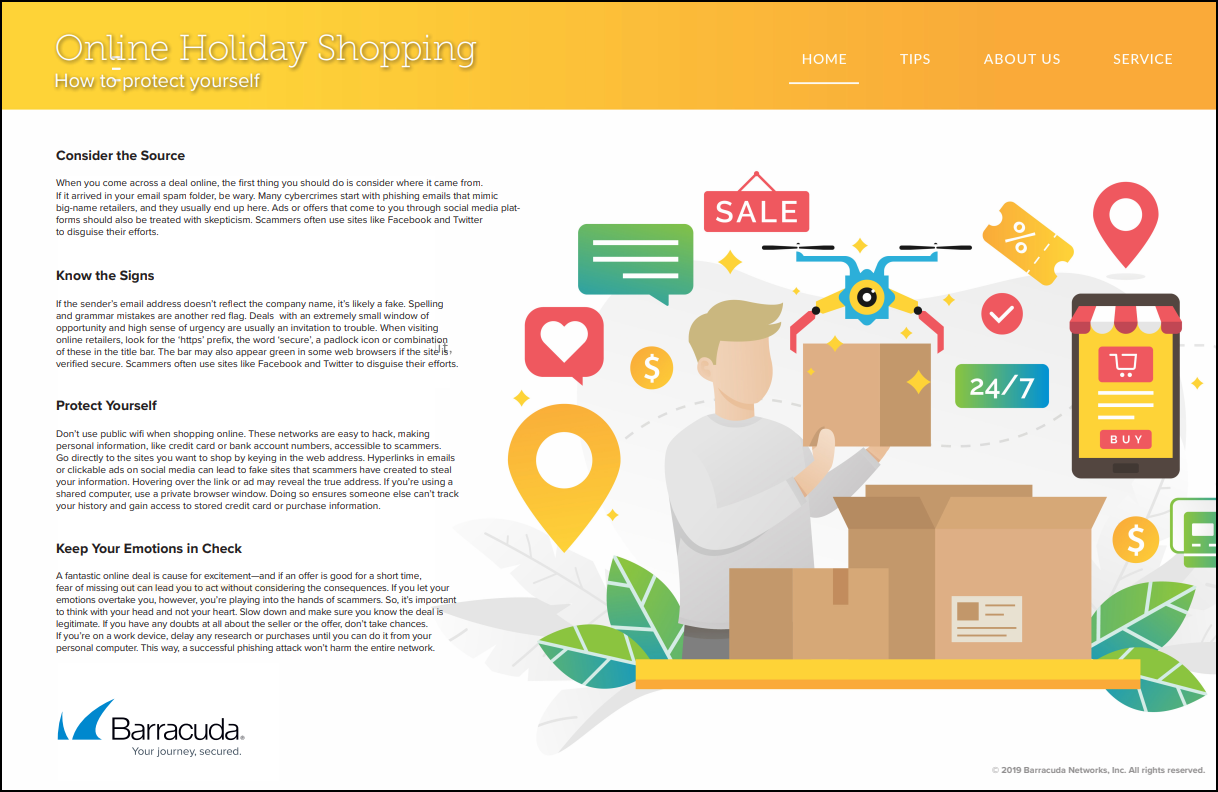
Online Holiday Shopping
Released November 2019
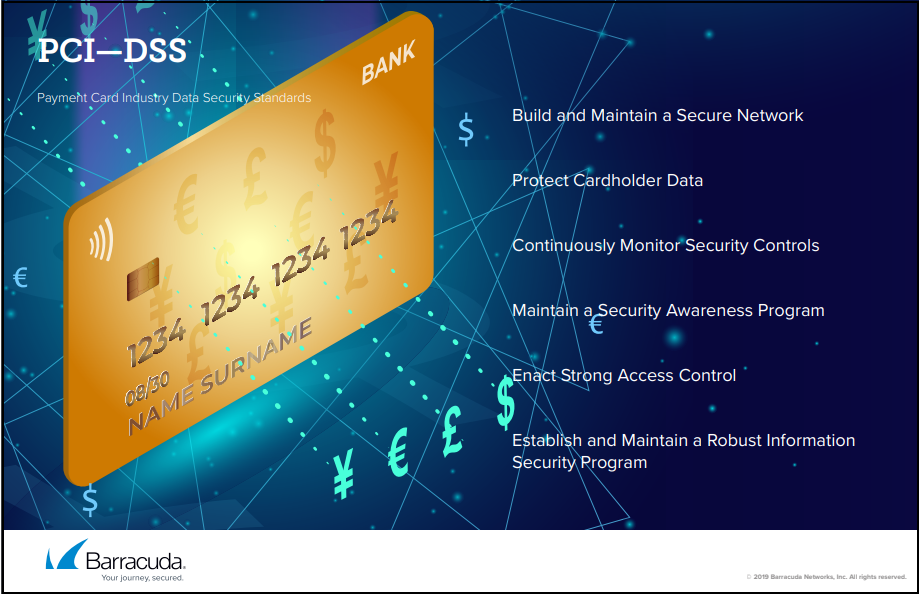
PCI-DSS
Released October 2019
GDPR
Released September 2019

Phishing Careers
Released June 2019

Catfishing
Released May 2019
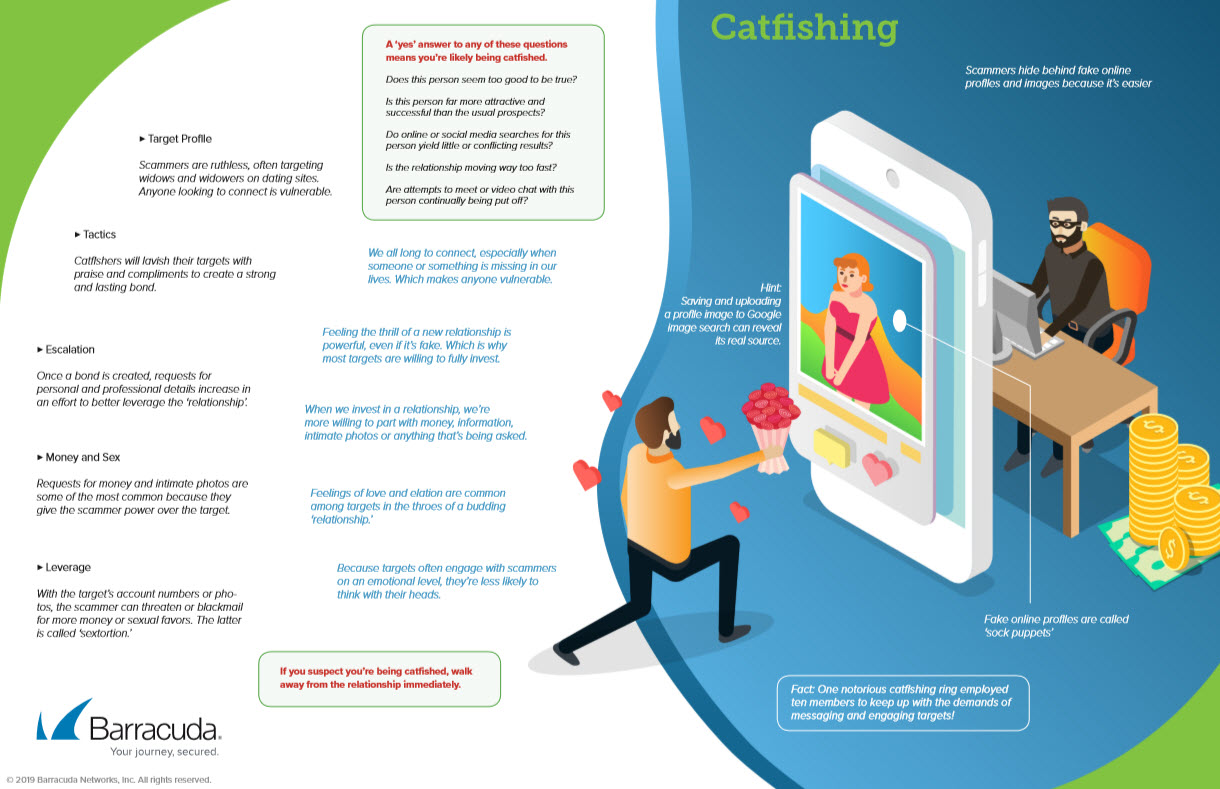
What is catfishing and how to detect it.
Executive Targeting
Released April 2019
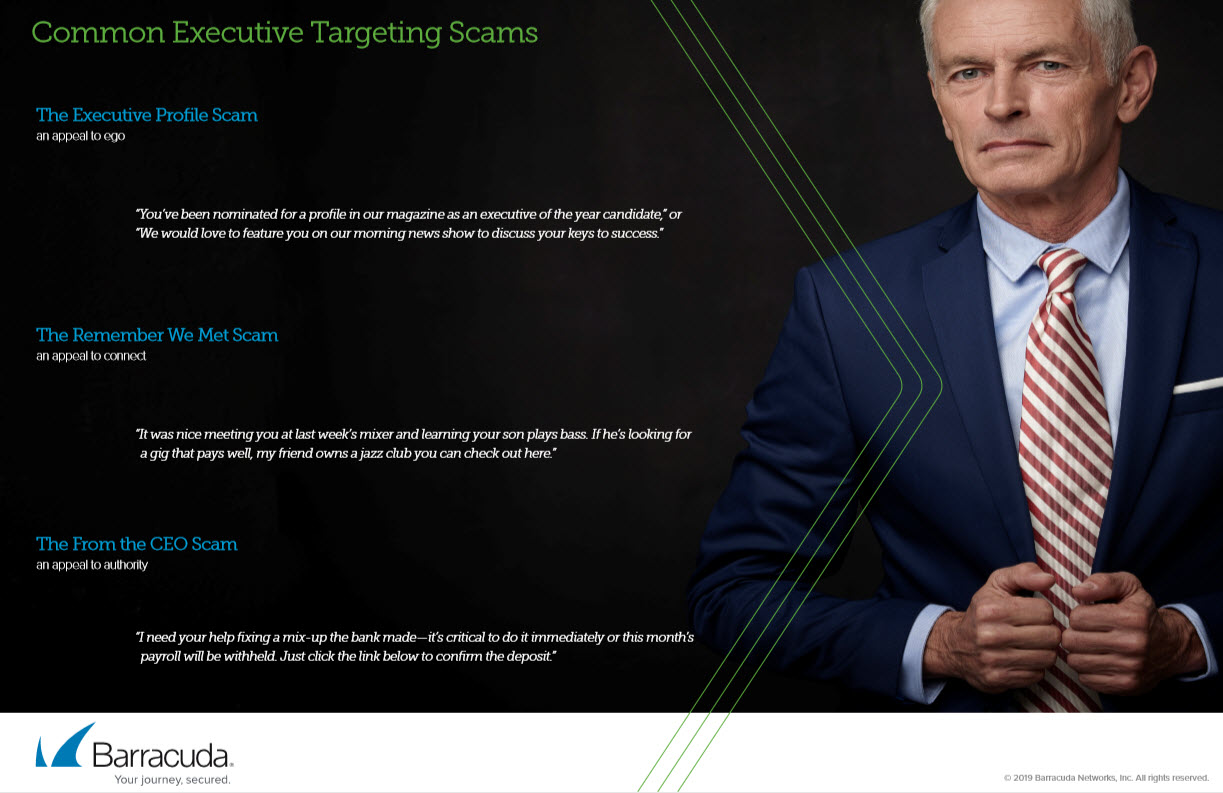
A look at why senior executives are not immune to social engineering and phishing attacks.
Working from Home
Released January 2019

Informs employees about safety while working from home.
Web Browsing and Work
Released December 2018

Informs employees about the risks and ramifications of browsing the web at work.
Internet of Things
Released November 2018
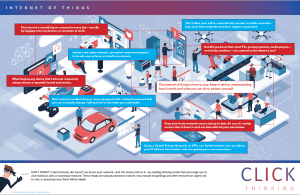
Alerts viewers to the risks of using internet-connected devices.
Public Wi-Fi
Released September 2018

A look at the risks of using public Wi-Fi and ways to protect yourself.
Bring Your Own Device (BYOD)
Released August 2018

Examines risks to using one device for both personal and business purposes.
Professional Networking
Released July 2018

Tips to protect you and your company when networking professionally.
Applications
Released June 2018

Explores the dangers of downloading apps from the Internet.
Personal and Physical Security
Released April 2018

We focus on personal and physical security concepts using fun personas to identify the types of tactics cybercriminals use to gain access to secure areas.
Travel and Out of Office
Released March 2018

An in-depth look at cybersecurity threats that can arise during business travel and ways to protect your data and company network while on the road.
Business Email Compromise
Released February 2018
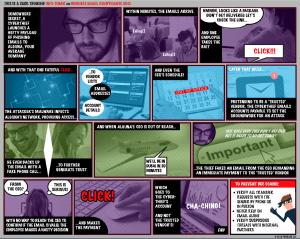
We examine how cybercriminals pull off business email compromise scams in an engaging and stylish comic-style format.
Personally Identifiable Information
Released January 2018
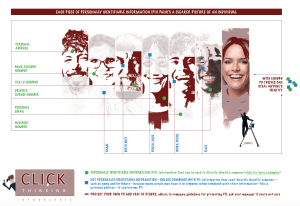
A look at what qualifies as personally identifiable information (PII) and how cybercriminals use it to commit crimes like identify theft.
2017 Archive
Click Thinking Bundle 1

Click Thinking Bundle 2

Click Thinking Bundle 3

Click Thinking Bundle 4
Click Thinking Bundle 5
Click Thinking Bundle 6

Signs of Phishing Animated GIF

This animated graphic changes every 10 seconds, so keep watching.
